Search for "14" returned 4693 results

30 min
Rowhammer.js: Root privileges for web apps?
A tale of fault attacks on DRAM and attacks on CPU caches

30 min
In Search of Evidence-Based IT-Security
IT security is largely a science-free field. This needs to…

33 min
Interplanetary Colonization
the state at the beginning of the 21st Century

30 min
Information Control and Strategic Violence
How governments use censorship and surveillance as part of…

30 min
Shut Up and Take My Money!
The Red Pill of N26 Security

33 min
Rebel Cities
Towards A Global Network Of Neighbourhoods And Cities…

29 min
Es sind die kleinen Dinge im Leben II
was alles geht und wie man anfängt, mit Mikroskopen

46 min
Practical Mix Network Design
Strong metadata protection for asynchronous messaging

43 min
This is NOT a proposal about mass surveillance!
Analysing the terminology of the UK’s Snooper’s Charter

57 min
TrustZone-M(eh): Breaking ARMv8-M's security
Hardware attacks on the latest generation of ARM Cortex-M…
22 min
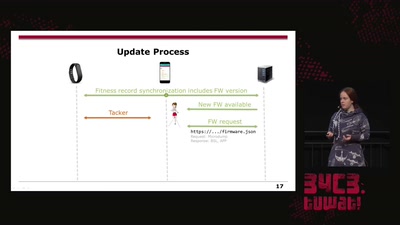
Doping your Fitbit
On Fitbit Firmware Modifications and Data Extraction
58 min
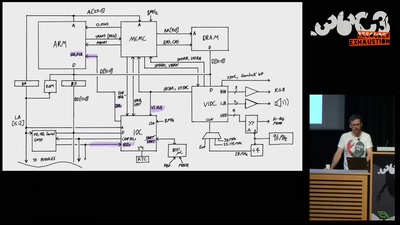
The Ultimate Acorn Archimedes talk
Everything about the Archimedes computer (with zero…
58 min
G10, BND-Gesetz und der effektive Schutz vor Grundrechten
Die strategische Fernmeldeüberwachung des BND vor dem…

26 min
Opening Event
35C3: Refreshing Memories

90 min
Security Nightmares
Damit Sie auch morgen schlecht von Ihrem Computer träumen.…

61 min
Beeinflussung durch Künstliche Intelligenz
Über die Banalität der Beeinflussung und das Leben mit…

50 min
How does the Internet work?
An explanation of Inter-Net and everyday protocols

63 min