Search for "30" returned 4248 results

46 min
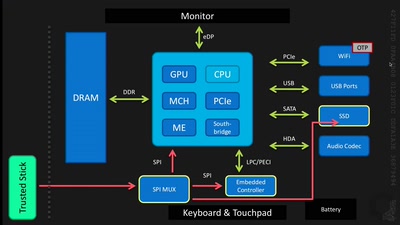
It's not safe on the streets... especially for your 3DS!
Exploring a new attack surface on the 3DS

54 min
CO2 Messen - in Raumen und in der Atmosphäre
Messmethoden für CO2-Ampel, Atmosphäre und mehr

45 min
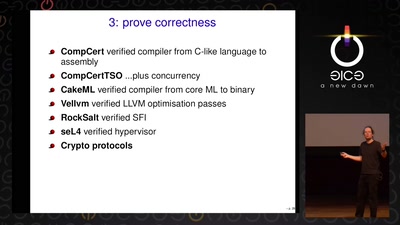
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache

44 min
Open Code Verlesung
Lesung des öffentlichen Sourcecodes

50 min
How does the Internet work?
An explanation of Inter-Net and everyday protocols

39 min
Web-based Cryptojacking in the Wild
When your browser is mining coins for other people

54 min
What Price the Upload Filter?
The history and costs of government exceptional access
31 min
Working together in one place with Nextcloud
What's scaring Big Tech today

13 min
OpenQA - review jobs and file bug report
OpenSUSE job review/bug report

60 min
Tiger, Drucker und ein Mahnmal
Neues vom Zentrum für Politische Schönheit

21 min
Another Approach to AI
An approach to ethical AI focussed on transparency and…

26 min