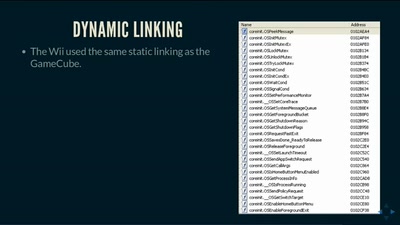
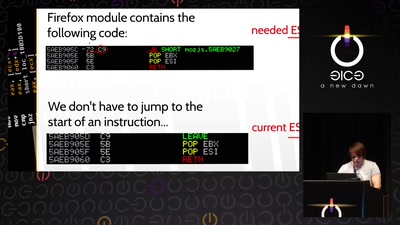
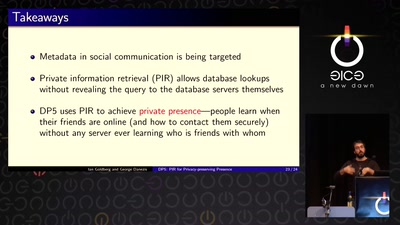
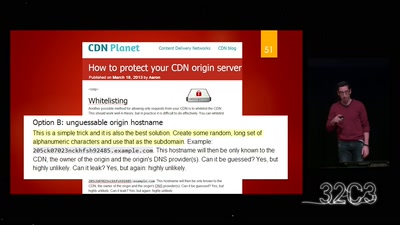
Search for "24" returned 4352 results
55 min
Cyber Necromancy
Reverse Engineering Dead Protocols

60 min
Windows drivers attack surface
some 'new' insights
64 min
3 Years After Snowden: Is Germany fighting State Surveillance?
A Closer Look at the Political Reactions to Mass…
60 min
Desperately Seeking Susy
A farewell to a bold proposal?
31 min
Access To Bodies
Ein Leitfaden für post-humane Computer- und…

62 min
Tell no-one
A century of secret deals between the NSA and the telecom…
65 min
Rocket science – how hard can it be?
First steps into space with sounding rockets

62 min
Transhuman Expression
Interdisciplinary research in Painting and Robotics. with…
32 min
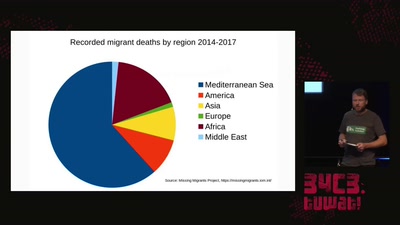
The seizure of the Iuventa
How search and rescue in the mediterranean was criminalized

61 min
Safe and Secure Drivers in High-Level Languages
How to write PCIe drivers in Rust, go, C#, Swift, Haskell,…
38 min
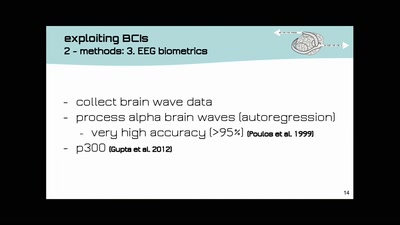
Open-BCI DIY-Neuroscience Maker-Art Mind-Hacking
open source DIY brain-computer-interfaces | technology and…

58 min
Überwachen und Sprache
How to do things with words

66 min
Die Drohnenkriege
Kriegsführung der Zukunft?

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

59 min