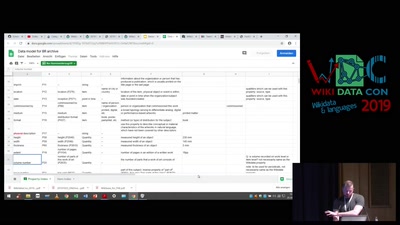
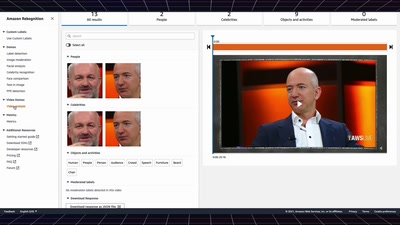
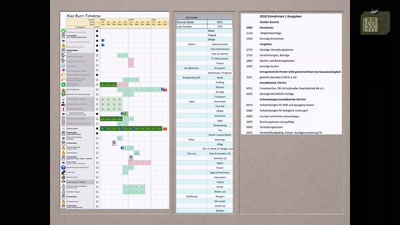
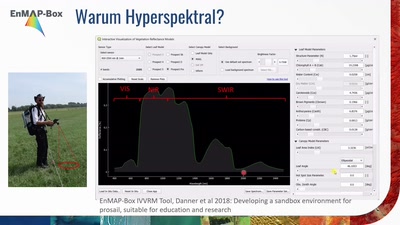
Search for "52" returned 3752 results

60 min
On the insecure nature of turbine control systems in power generation
A security study of turbine control systems in power…

58 min
CIA vs. Wikileaks
Intimiditation surveillance and other tactics observed and…

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

61 min
An Elevator to the Moon (and back)
Space Transportation and the Extraterrestrial Imperative

57 min
"Fluxus cannot save the world."
What hacking has to do with avantgarde art of the 1960ies…
62 min
Public Library/Memory of the World
Access to knowledge for every member of society

57 min