Search for "19" returned 4612 results

58 min
Thwarting Evil Maid Attacks
Physically Unclonable Functions for Hardware Tamper…
32 min
The seizure of the Iuventa
How search and rescue in the mediterranean was criminalized

63 min
The Global Assassination Grid
The Infrastructure and People behind Drone Killings

50 min
How does the Internet work?
An explanation of Inter-Net and everyday protocols

60 min
The Critical Making Movement
How using critical thinking in technological practice can…

60 min
Hacking Reality
Mixed Reality and multi-sensory communication

63 min
Reconstructing narratives
transparency in the service of justice

62 min
„Wir beteiligen uns aktiv an den Diskussionen“
Die digitale „Agenda“ der Bundesregierung aus inhaltlicher,…
60 min
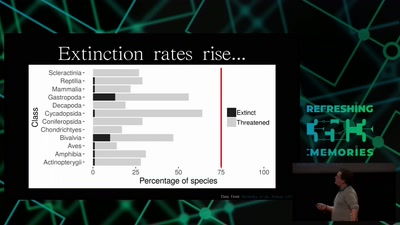
Hacking Ecology
How Data Scientists can help to avoid a sixth global…

60 min
Are machines feminine?
exploring the relations between design and perception of…
59 min
Top X* usability obstacles
*(will be specified later based on usability test with…

60 min
Hardware-Trojaner in Security-Chips
Eine Reise auf die dunkle Seite
33 min
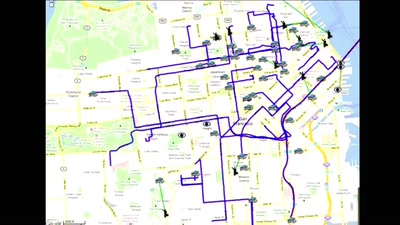
Space making/space shaping
How mapping creates space, shapes cities and our view of…

41 min
NGI Zero: A treasure trove of IT innovation
Resilient. Trustworthy. Sustainably Open.
60 min