Search for "19" returned 4609 results

59 min
Provable Security
How I learned to stop worrying and love the backdoor
55 min
Cat & Mouse: Evading the Censors in 2018
Preserving access to the open Internet with circumvention…
40 min
No roborders, no nation, or: smile for a European surveillance propagation
How an agency implements Fortress Europe by degrading…

40 min
Radical Digital Painting
Fantastic Media Manipulation

40 min
An introduction to Firmware Analysis
Techniques - Tools - Tricks

47 min
Hardening hardware and choosing a #goodBIOS
Clean boot every boot - rejecting persistence of malicious…

60 min
osmo-gmr: What's up with sat-phones ?
Piecing together the missing bits

58 min
CIA vs. Wikileaks
Intimiditation surveillance and other tactics observed and…

64 min
"Exploit" in theater
post-existentialism is the question, not post-privacy
50 min
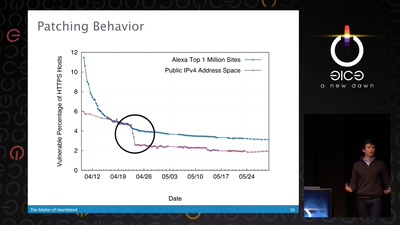
The Matter of Heartbleed
What went wrong, how the Internet reacted, what we can…

57 min
"Fluxus cannot save the world."
What hacking has to do with avantgarde art of the 1960ies…

61 min
An Elevator to the Moon (and back)
Space Transportation and the Extraterrestrial Imperative

58 min
PLC-Blaster
Ein Computerwurm für PLCs

60 min
Lets break modern binary code obfuscation
A semantics based approach

60 min
The rise and fall of Internet voting in Norway
Evaluating a complex cryptographic implementation

59 min