Search for "13" returned 4826 results

29 min
lasers in space
more than just pew pew!

58 min
How risky is the software you use?
CITL: Quantitative, Comparable Software Risk Reporting

60 min
Shopshifting
The potential for payment system abuse

41 min
Locked up science
Tearing down paywalls in scholarly communication

49 min
Key-logger, Video, Mouse
How to turn your KVM into a raging key-logging monster

60 min
the possibility of an army
phone verified accounts bringing the Hessian army back to…

57 min
The Layman's Guide to Zero-Day Engineering
A demystification of the exploit development lifecycle

44 min
Disclosure DOs, Disclosure DON'Ts
Pragmatic Advice for Security Researchers

47 min
Bug class genocide
Applying science to eliminate 100% of buffer overflows
53 min
The Ultimate Amiga 500 Talk
Amiga Hardware Design And Programming

63 min
Das nützlich-unbedenklich Spektrum
Können wir Software bauen, die nützlich /und/ unbedenklich…
60 min
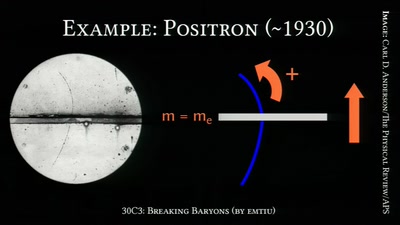
Breaking Baryons
On the Awesomeness of Particle Accelerators and Colliders

64 min
Decoding the LoRa PHY
Dissecting a Modern Wireless Network for the Internet of…

49 min
BREACH in Agda
Security notions, proofs and attacks using dependently…

60 min