Search for "11" returned 4577 results

39 min
Web-based Cryptojacking in the Wild
When your browser is mining coins for other people
58 min
RFID Treehouse of Horror
Hacking City-Wide Access Control Systems

42 min
A world without blockchain
How (inter)national money transfers works

45 min
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache

61 min
Ten years after ‚We Lost The War‘
The future does not look much brighter than ten years ago.…
64 min
Der Deep Learning Hype
Wie lange kann es so weitergehen?
60 min
„Nach bestem Wissen und Gewissen“ – Floskeln in der Politik
Politische Phrasologie – warum man aus dem ganzen Zeug, das…

60 min
Ich sehe, also bin ich ... Du
Gefahren von Kameras für (biometrische)…

53 min
No Love for the US Gov.
Why Lauri Love’s case is even more important than you…
61 min
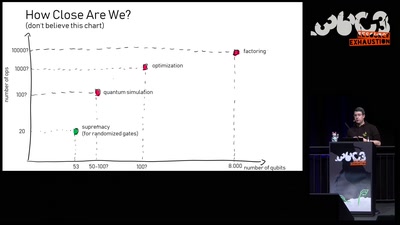
Quantum Computing: Are we there yet?
An introduction to quantum computing and a review of the…

54 min
AMD x86 SMU firmware analysis
Do you care about Matroshka processors?

85 min
Erklär ma:
Solarenergie

66 min
Keine Anhaltspunkte für flächendeckende Überwachung
Die Diskussion um NSA, PRISM, Tempora sprachlich und…

58 min