Search for "19" returned 4472 results
72 min
State of the Onion
Neuland

58 min
How risky is the software you use?
CITL: Quantitative, Comparable Software Risk Reporting

44 min
What the cyberoptimists got wrong - and what to do about it
Tech unexeptionalism and the monopolization of every…

56 min
WarGames in memory
what is the winning move?

57 min
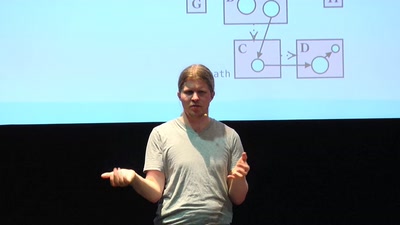
The Layman's Guide to Zero-Day Engineering
A demystification of the exploit development lifecycle

60 min
Best of Informationsfreiheit
Transparenz mit der Brechstange

55 min
The DROWN Attack
Breaking TLS using SSLv2

62 min
The Internet (Doesn't) Need Another Security Guide
Creating Internet Privacy and Security Resources That Don't…

60 min
From Computation to Consciousness
How computation helps to explain mind, universe and…

60 min
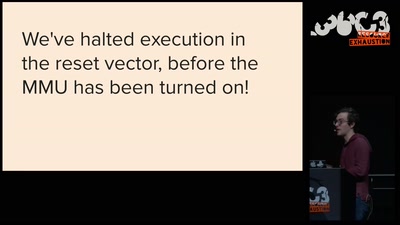
Check your privileges!
How to drop more of your privileges to reduce attack…

62 min