Search for "Noa" returned 4318 results

29 min
Infocalypse now: P0wning stuff is not enough
Several failure modes of the hacker scene
34 min
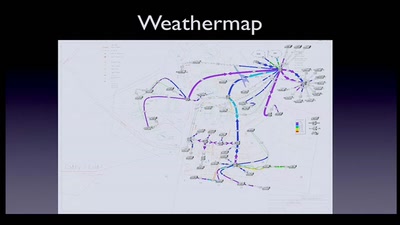
NOC Review
NOC Review about the Camp 2011 and the 28C3

6 min
Not a game
München
38 min
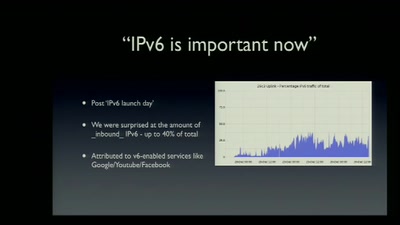
NOC Review
NOC Review about the 29C3
31 min
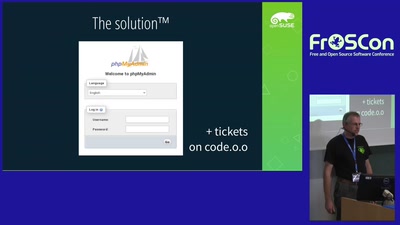
Still not Superheroes
Was die openSUSE Admins lieber nicht verraten würden
41 min
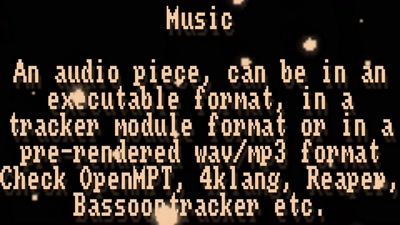
Demoscene now and then
The demoscene is an underground computer art culture.

31 min
TrustZone is not enough
Hijacking debug components for embedded security

27 min