Search for ".uje" returned 3167 results

56 min
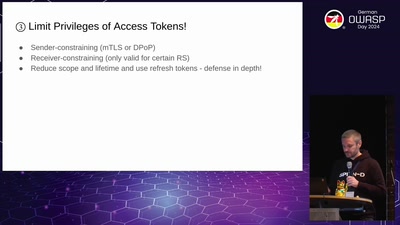
How not to use OAuth
New security recommendations for OAuth
49 min
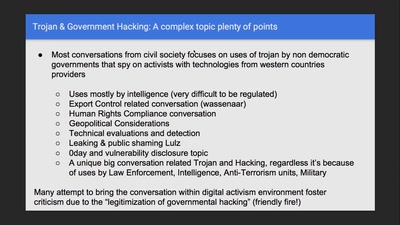
Regulating Law Enforcement use of Trojans
Implementing a Law to juridically, operationally and…
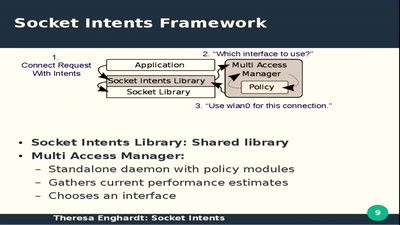
39 min
Which network to use when - Socket Intents
Hacking the Socket API for fun and research

58 min
How risky is the software you use?
CITL: Quantitative, Comparable Software Risk Reporting

38 min
Designing a 3D printed tool for medical use
From reverse engineering to iterative design

44 min
Fantastic Arm boards and how to use them
News on hardware and Spectre
30 min