Search for "Thde" returned 8451 results
52 min
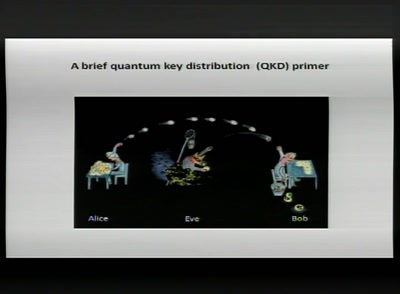
How you can build an eavesdropper for a quantum cryptosystem
hardware demo during the lecture

49 min
"What's in a name?"
#nymwars and the public sphere

56 min
Desperate House-Hackers
How to Hack the Pfandsystem

31 min
A Tale of Two Leaks:
How Hackers Breached the Great Firewall of China

41 min
Ten Years of Rowhammer:
A Retrospect (and Path to the Future)

87 min
OPENCOIL – A Roaming Speedshow
or the fine art of appropriating inductive charging pads in…
60 min
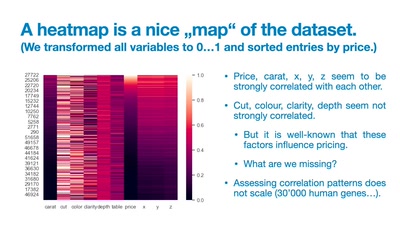
Patterns in Chaos:
How Data Visualisation Helps To See the Invisible
52 min
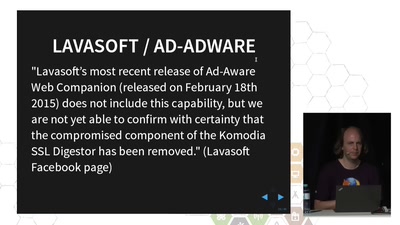
TLS interception considered harmful
How Man-in-the-Middle filtering solutions harm the security…

60 min
Are machines feminine?
exploring the relations between design and perception of…

63 min
Counter-Development
The Accessibility of Technology as an Addendum to…
34 min
FeTAp 611 unplugged
Taking a rotary dial phone to the mobile age

36 min
What I Learned from Loab: AI as a creative adversary
The artist behind the viral cryptid "Loab" reflects on her…

46 min
Climate Modelling
The Science Behind Climate Reports

23 min
Using BPF in Kubernetes
Linux superpowers in the cloud

39 min
Domain Driven Design & NoSQL
Escaping the Tower of Babel

56 min
WarGames in memory
what is the winning move?

55 min
Encrypted Email for Planet Earth
Failures, Challenges, and the Future

58 min
Virtual Machine Introspection
From the Outside Looking In

41 min
Corona-Warn-App
Behind the scenes: Invisible, yet important

56 min
Viva la Vita Vida
Hacking the most secure handheld console

17 min
Lightning Talks
Submit Your Talks at the Venue
25 min