Search for ".hop" returned 4672 results

49 min
Syscall proxying fun and applications
Introduction to syscall proxying and applications for in…

30 min
Privacy and Consumer Markets
Reversing the Surveillance Business Model

39 min
The automobile as massive data gathering source and the consequences for individual…
The next big privacy heist

12 min
Making a practicle VNC client for character terminals
Digs into terminal programming in depth, and demonstrates…

61 min
Design and Implementation of an object-oriented, secure TCP/IP Stack
Ethereal^W Wireshark without remote exploits - a proof of…
35 min
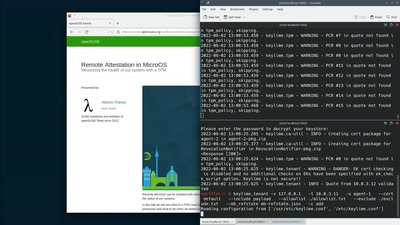
Remote Attestation in MicroOS
Measuring the health of our system with a TPM
31 min
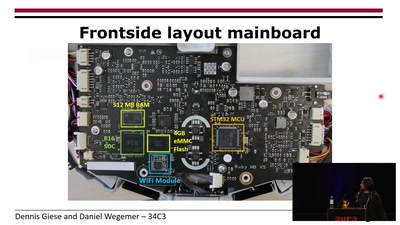
Unleash your smart-home devices: Vacuum Cleaning Robot Hacking
Why is my vacuum as powerful as my smartphone?
43 min
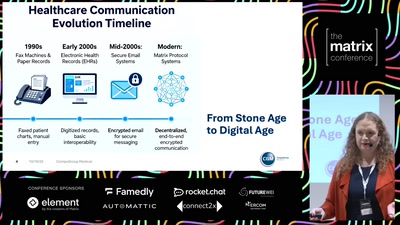
Matrix as a Bridge
Enabling Cross-Border Healthcare Communication Through Open…

27 min
The law and leaky abstractions
In what ways can laws influence the security of society.

58 min
Baseband Exploitation in 2013
Hexagon challenges

62 min
![A gentle introduction to [e]BPF](https://static.media.ccc.de/media/events/all_systems_go/2017/92-hd.jpg)