Search for ".dol" returned 2575 results

39 min
The automobile as massive data gathering source and the consequences for individual…
The next big privacy heist

30 min
In Search of Evidence-Based IT-Security
IT security is largely a science-free field. This needs to…
60 min
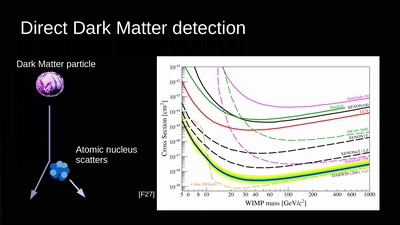
Let's reverse engineer the Universe
exploring the dark
30 min
Automatically Subtitling the C3
How speech processing helps the CCC subtitle project, and…

30 min
Shut Up and Take My Money!
The Red Pill of N26 Security

58 min
When hardware must „just work“
An inside look at x86 CPU design
31 min
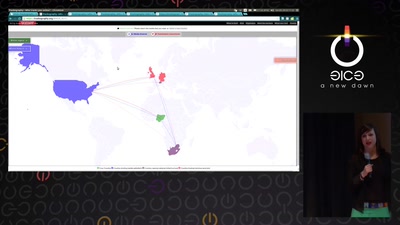
Trackography
You never read alone
32 min
library operating systems
reject the default reality^W abstractions and substitute…

63 min
goto fail;
exploring two decades of transport layer insecurity
22 min
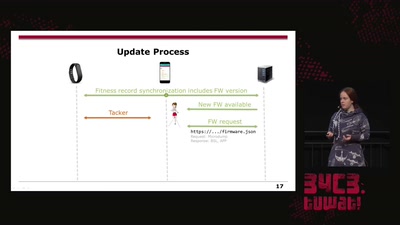
Doping your Fitbit
On Fitbit Firmware Modifications and Data Extraction

30 min
Rowhammer.js: Root privileges for web apps?
A tale of fault attacks on DRAM and attacks on CPU caches

60 min
Internet Cube
Let's Build together a Free, Neutral and Decentralized…

30 min
Syrian Archive
Preserving documentation of human rights violations
31 min
The Economic Consequences of Internet Censorship
Why Censorship is a Bad Idea for Everyone

34 min