Search for "id4=WPnt" returned 320 results

60 min
Adventures in Reverse Engineering Broadcom NIC Firmware
Unlocking a system with 100% open source firmware

72 min
Console Hacking
Breaking the 3DS

46 min
SELECT code_execution FROM * USING SQLite;
--Gaining code execution using a malicious SQLite database

29 min
Pegasus internals
Technical Teardown of the Pegasus malware and Trident…

60 min
The Exploration and Exploitation of an SD Memory Card
by xobs & bunnie
39 min
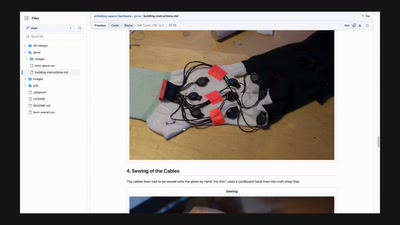
The Unfolding Space Glove
A Wearable for the Visually Impaired Translating 3D Vision…

59 min
Financial surveillance
Exposing the global banking watchlist

60 min
Everything you always wanted to know about Certificate Transparency
(but were afraid to ask)

44 min
Disclosure DOs, Disclosure DON'Ts
Pragmatic Advice for Security Researchers

31 min
TrustZone is not enough
Hijacking debug components for embedded security
55 min
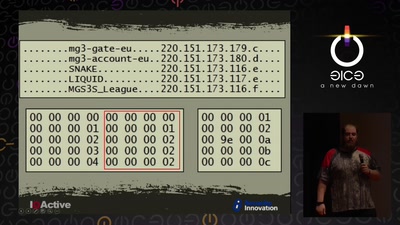
Cyber Necromancy
Reverse Engineering Dead Protocols
62 min
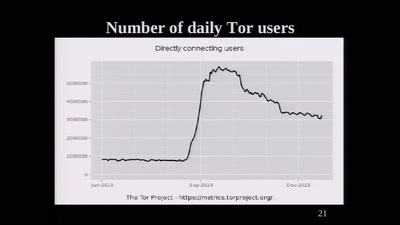
The Tor Network
We're living in interesting times
38 min
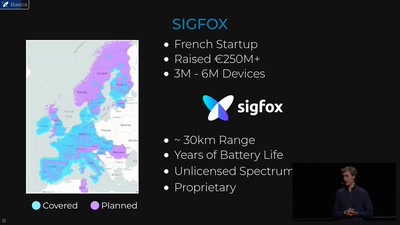
Hunting the Sigfox: Wireless IoT Network Security
Dissecting the radio protocol of Sigfox, the global…

30 min
Forging the USB armory
Creating an open source secure flash-drive-sized computer

60 min
APT Reports and OPSEC Evolution, or: These are not the APT reports you are looking for
How advanced threat actors learn and change with innovation…
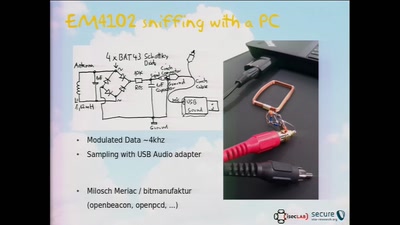
58 min