Search for "Andi" returned 7270 results

50 min
How does the Internet work?
An explanation of Inter-Net and everyday protocols

59 min
Pointing Fingers at 'The Media'
The Bundestagswahl 2017 and Rise of the AfD

49 min
Electromagnetic Threats for Information Security
Ways to Chaos in Digital and Analogue Electronics
39 min
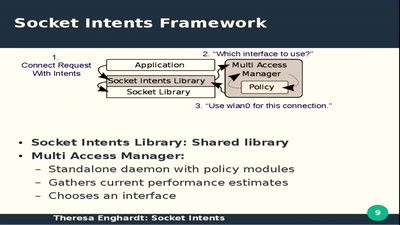
Which network to use when - Socket Intents
Hacking the Socket API for fun and research

28 min
Governing the data lake
Data governance and security for your precious data.

57 min
Why Net Neutrality Matters?
Status update on current legislation, campaigns and actions

30 min
A Torifying Tale
Our experiences of building and running Tor servers

54 min
World War II Hackers
Stalin's best men, armed with paper and pen
55 min
SigOver + alpha
Signal overshadowing attack on LTE and its applications
42 min
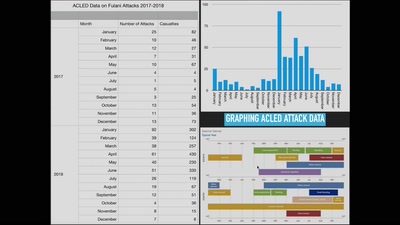
Mapping Doomsday
Using OSINT to monitor and predict environmental conflicts
41 min
State of Ceph
What's new in Nautilus and what's coming next?
37 min
Inside the AMD Microcode ROM
(Ab)Using AMD Microcode for fun and security

22 min
What's new in OBS?
Latest new features and how to use them
50 min
GNU Health on openSUSE - a community view
Insights into a global, diverse and friendly community

55 min
The Future of Virtualization
The "anyOS" paradigm and its implications through…

49 min
Lawful Interception in VoIP networks
Old Laws and New Technology the German Way
60 min
Breaking Baryons
On the Awesomeness of Particle Accelerators and Colliders
39 min
Cybernetics for the Masses
implants, sensory extension and silicon - all for you!
59 min
Pushing the limits of DIY electronics
Bridging the gap between DIY and professional electronics

62 min
Transhuman Expression
Interdisciplinary research in Painting and Robotics. with…
39 min
Making homebrew for your very own Vector Super Computer
Adventures running a NEC Vector Engine for fun and ...…

42 min
NEW IMPORTANT INSTRUCTIONS
Real-world exploits and mitigations in Large Language Model…

38 min
The impact of quantum computers in cybersecurity
Estimating the costs of algorithms for attacks and defense…

41 min
Breathing Life into Legacy: An Open-Source Emulator of Legacy Apple Devices
A Dive into Reverse Engineering and Understanding the iPod…

54 min