Search for "535" returned 2044 results

55 min
The DROWN Attack
Breaking TLS using SSLv2
63 min
Kritikalität von Rohstoffen - wann platzt die Bombe?
Ein nicht nuklearer Blick auf das Ende der Welt

63 min
Das nützlich-unbedenklich Spektrum
Können wir Software bauen, die nützlich /und/ unbedenklich…

44 min
Disclosure DOs, Disclosure DON'Ts
Pragmatic Advice for Security Researchers

47 min
Bug class genocide
Applying science to eliminate 100% of buffer overflows
60 min
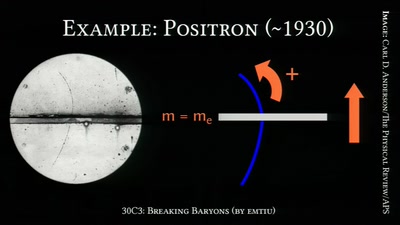
Breaking Baryons
On the Awesomeness of Particle Accelerators and Colliders

64 min
Decoding the LoRa PHY
Dissecting a Modern Wireless Network for the Internet of…

49 min
Key-logger, Video, Mouse
How to turn your KVM into a raging key-logging monster
62 min
Getting software right with properties, generated tests, and proofs
Evolve your hack into robust software!
59 min
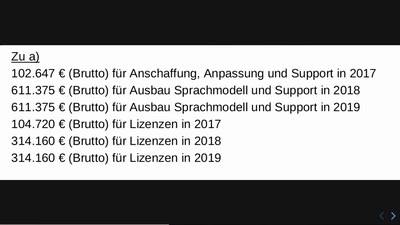
Computer, die über Asyl (mit)entscheiden
Wie das BAMF seine Probleme mit Technik lösen wollte und…
53 min
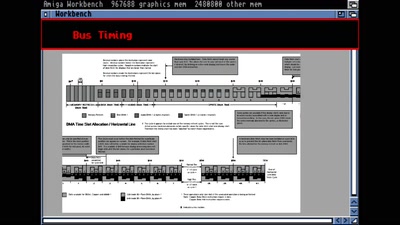
The Ultimate Amiga 500 Talk
Amiga Hardware Design And Programming

62 min
To Protect And Infect, Part 2
The militarization of the Internet

53 min
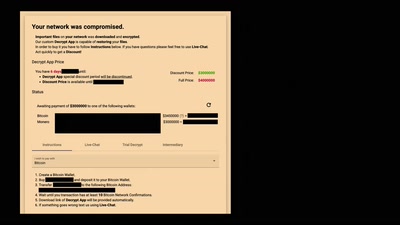
Console Hacking 2016
PS4: PC Master Race
61 min