Search for "Liv" returned 1621 results

32 min
History and implications of DRM
From tractors to Web standards

61 min
Code Pointer Integrity
... or how we battle the daemons of memory safety

42 min
A world without blockchain
How (inter)national money transfers works
62 min
Getting software right with properties, generated tests, and proofs
Evolve your hack into robust software!
55 min
SigOver + alpha
Signal overshadowing attack on LTE and its applications
59 min
The Surveillance State limited by acts of courage and conscience
An update on the fate of the Snowden Refugees

58 min
How risky is the software you use?
CITL: Quantitative, Comparable Software Risk Reporting

44 min
Disclosure DOs, Disclosure DON'Ts
Pragmatic Advice for Security Researchers
59 min
Election Cybersecurity Progress Report
Will the U.S. be ready for 2020?
36 min
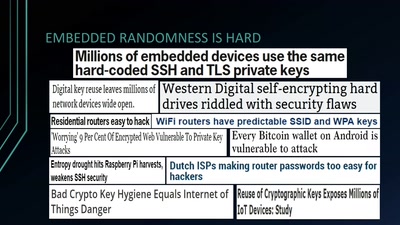
Wheel of Fortune
Analyzing Embedded OS Random Number Generators

62 min
Space Ops 101
An introduction to Spacecraft Operations

63 min
Das nützlich-unbedenklich Spektrum
Können wir Software bauen, die nützlich /und/ unbedenklich…
57 min
A New Dark Age
Turbulence, Big Data, AI, Fake News, and Peak Knowledge

60 min
![Why we are addicted to lithium [1/2]](https://static.media.ccc.de/media/events/rc3/2021/193-3fd1b8af-9ab6-54c5-88ad-2622c1cc925a.jpg)



![failed: [Inklusion]](https://static.media.ccc.de/media/conferences/divoc/r2r/7-28904449-d357-566f-97ef-86ade89f9395.jpg)

