Search for "357" returned 1995 results

46 min
You can -j REJECT but you can not hide: Global scanning of the IPv6 Internet
Finding interesting targets in 128bit of entropy
60 min
Software Defined Emissions
A hacker’s review of Dieselgate
62 min
A New Kid on the Block
Conditions for a Successful Market Entry of Decentralized…

39 min
ID Cards in China: Your Worst Nightmare
In China Your ID Card Knows Everything

60 min
Hardware-Trojaner in Security-Chips
Eine Reise auf die dunkle Seite

46 min
CounterStrike
Lawful Interception
38 min
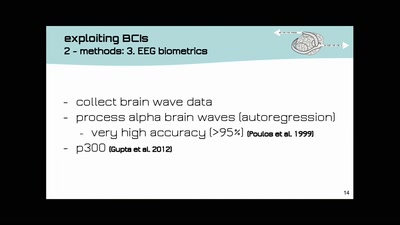
Open-BCI DIY-Neuroscience Maker-Art Mind-Hacking
open source DIY brain-computer-interfaces | technology and…

60 min
Lets break modern binary code obfuscation
A semantics based approach

62 min
radare demystified
after 1.0

60 min
The rise and fall of Internet voting in Norway
Evaluating a complex cryptographic implementation

64 min
"Exploit" in theater
post-existentialism is the question, not post-privacy

60 min
The Only Thing We Know About Cyberspace Is That Its 640x480
One Terabyte of Kilobyte Age

59 min
Hacking EU funding for a decentralizing FOSS project
Understanding and adapting EU legal guidelines from a FOSS…

55 min
3D Casting Aluminum
Too Much Fun with Microwaves

57 min
Kryptographie nach Snowden
Was tun nach der mittelmäßigen Kryptographie-Apokalypse?
38 min
Unpacking the compromises of Aadhaar, and other digital identities inspired by it
Governments around the world are implementing digital…
40 min
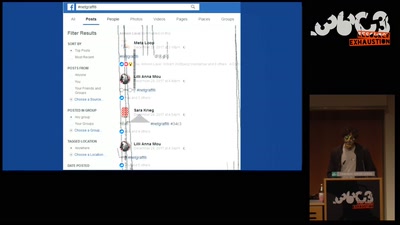
Art against Facebook
Graffiti in the ruins of the feed and the…
42 min