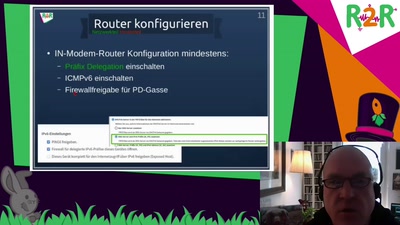
Search for "id4=WPnt" returned 320 results

46 min
CounterStrike
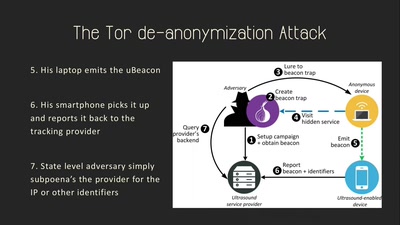
Lawful Interception
16 min
Decent Patterns
an Open UX Library for Decentralisation
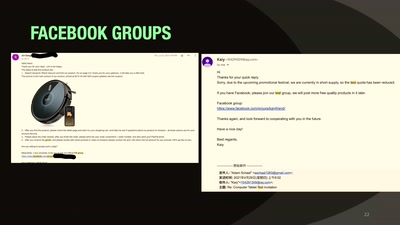
41 min
Our Time in a Product Review Cabal
And the malware and backdoors that came with it.

40 min
A year of surveillance in France: a short satirical tale by La Quadrature du Net
From the so-called Country of human rights to a…

30 min
Shut Up and Take My Money!
The Red Pill of N26 Security

60 min
The plain simple reality of entropy
Or how I learned to stop worrying and love urandom

56 min
Reality Check! Basel/Lagos?? In virtual reality?
An African tale of art, culture and technology

46 min
Writing secure software
using my blog as example

30 min
The Machine To Be Another
Exploring identity and empathy through neuroscience,…

58 min
How risky is the software you use?
CITL: Quantitative, Comparable Software Risk Reporting

38 min
What your phone won’t tell you
Uncovering fake base stations on iOS devices
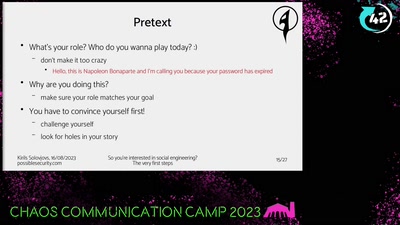
44 min
So you're interested in social engineering?
The very first steps

33 min
Gone in 60 Milliseconds
Intrusion and Exfiltration in Server-less Architectures
59 min