Search for "358" returned 2013 results

46 min
Electronic Evicence in Criminal Matters
An introduction and critique of the EC proposal for a…

51 min
Virtual Secure Boot
Secure Boot support in qemu, kvm and ovmf.

63 min
A look into the Mobile Messaging Black Box
A gentle introduction to mobile messaging and subsequent…

41 min
Extracting keys from FPGAs, OTP Tokens and Door Locks
Side-Channel (and other) Attacks in Practice

58 min
Switches Get Stitches
Industrial System Ownership

49 min
Dissecting VoLTE
Exploiting Free Data Channels and Security Problems

61 min
How Alice and Bob meet if they don't like onions
Survey of Network Anonymisation Techniques
55 min
3D printing on the moon
The future of space exploration

56 min
Household, Totalitarianism and Cyberspace
Philosophical Perspectives on Privacy Drawing on the…

55 min
Inside Field Station Berlin Teufelsberg
The story of the NSA listening post – told by an ex-SIGINT…

62 min
Mensch - Kunst – Maschine
Mit künstlicher Intelligenz zu neuer Kunst zum…
40 min
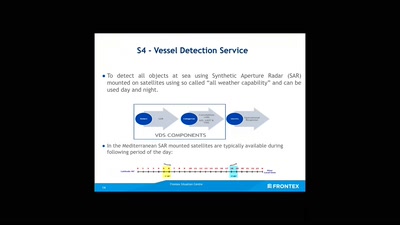
No roborders, no nation, or: smile for a European surveillance propagation
How an agency implements Fortress Europe by degrading…
56 min