Search for "149" returned 2418 results

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities
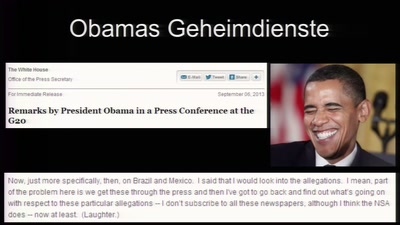
117 min
Fnord News Show
Der schonungslose Realitätsabgleich mit…
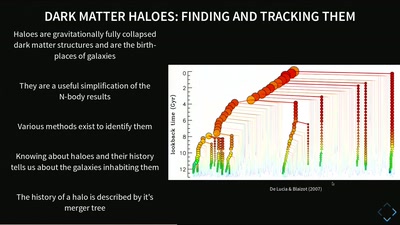
60 min
Simulating Universes
What Virtual Universes Can Tell Us About Our Own
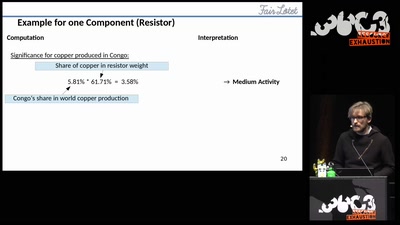
38 min
Fairtronics
A Tool for Analyzing the Fairness of Electronic Devices
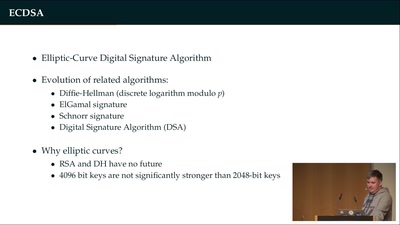
35 min
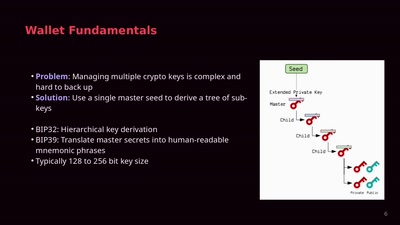
Wallet Security
How (not) to protect private keys
39 min
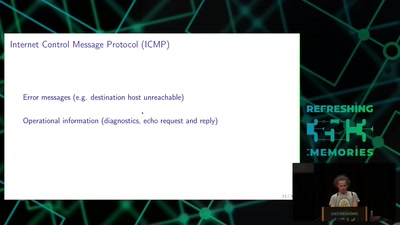
Transmission Control Protocol
TCP/IP basics
35 min
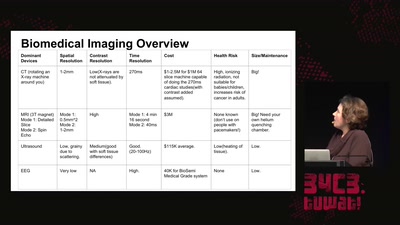
Low Cost Non-Invasive Biomedical Imaging
An Open Electrical Impedance Tomography Project

31 min
JODI - Apache is functioning normally
A net.art collective since 1995. Understanding the browser…

59 min
Memory Deduplication: The Curse that Keeps on Giving
A tale of 3 different memory deduplication based…

57 min
How I Learned to Stop Reinventing and Love the Wheels
or having FUN with (home/hackerspace) robotics

55 min
White-Box Cryptography
Survey

61 min
How Alice and Bob meet if they don't like onions
Survey of Network Anonymisation Techniques
62 min
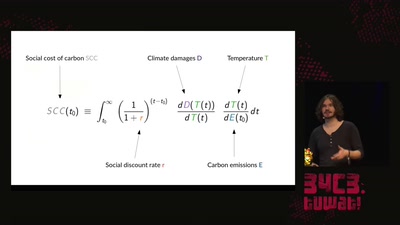
A hacker's guide to Climate Change - What do we know and how do we know it?
An introduction to the basics of climate research and what…

60 min