Search for "Remote" returned 1059 results

45 min
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache

59 min
Hardsploit: A Metasploit-like tool for hardware hacking
A complete toolbox for IoT security

90 min
Security Nightmares
Damit Sie auch morgen schlecht von Ihrem Computer träumen.…

65 min
Mind-Hacking mit Psychedelika
Eine Einführung in die Wirkungsweise psychedelischer…
53 min
The Ultimate Amiga 500 Talk
Amiga Hardware Design And Programming

51 min
Funky File Formats
Advanced binary tricks

63 min
Reproducible Builds
Moving Beyond Single Points of Failure for Software…

58 min
When hardware must „just work“
An inside look at x86 CPU design

59 min
TamaGo - bare metal Go framework for ARM SoCs.
Reducing the attack surface with pure embedded Go.

60 min
The Only Thing We Know About Cyberspace Is That Its 640x480
One Terabyte of Kilobyte Age

55 min
3D Casting Aluminum
Too Much Fun with Microwaves

53 min
No Love for the US Gov.
Why Lauri Love’s case is even more important than you…
58 min
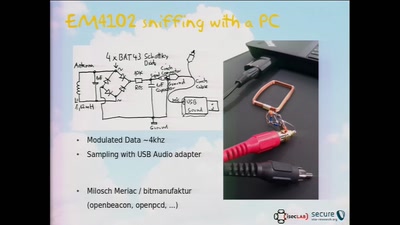
RFID Treehouse of Horror
Hacking City-Wide Access Control Systems
44 min
Replication Prohibited
3D printed key attacks

54 min
AMD x86 SMU firmware analysis
Do you care about Matroshka processors?

62 min
Let's Encrypt
A Free Robotic Certificate Authority

55 min