Search for ".egd" returned 1555 results

45 min
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache
36 min
Wheel of Fortune
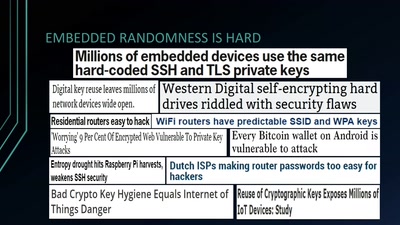
Analyzing Embedded OS Random Number Generators
60 min
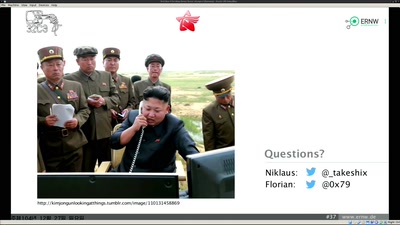
Lifting the Fog on Red Star OS
A deep dive into the surveillance features of North Korea's…

62 min
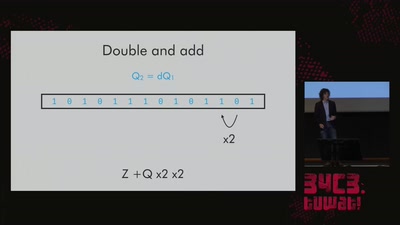
Kyber and Post-Quantum Crypto
How does it work?

60 min
Windows drivers attack surface
some 'new' insights

57 min
The Layman's Guide to Zero-Day Engineering
A demystification of the exploit development lifecycle
43 min
No PoC? No Fix! - A sad Story about Bluetooth Security
It is just a broken memcpy in the Bluetooth stack. Do we…

26 min
Humans as software extensions
Will You Be My Plugin?

49 min
BREACH in Agda
Security notions, proofs and attacks using dependently…
60 min
An ultrashort history of ultrafast imaging
Featuring the shortest movies and the largest lasers

61 min
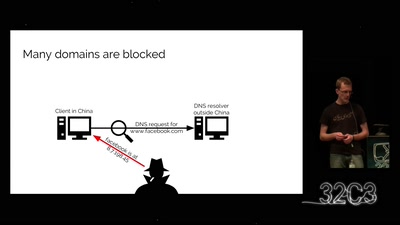
Now I sprinkle thee with crypto dust
Internet reengineering session

32 min