Search for "366" returned 1944 results

30 min
In Search of Evidence-Based IT-Security
IT security is largely a science-free field. This needs to…

33 min
Rebel Cities
Towards A Global Network Of Neighbourhoods And Cities…

30 min
Rowhammer.js: Root privileges for web apps?
A tale of fault attacks on DRAM and attacks on CPU caches

30 min
Information Control and Strategic Violence
How governments use censorship and surveillance as part of…

54 min
Do You Think That's Funny?
Art Practice under the Regime of Anti-Terror Legislation

61 min
How Alice and Bob meet if they don't like onions
Survey of Network Anonymisation Techniques
55 min
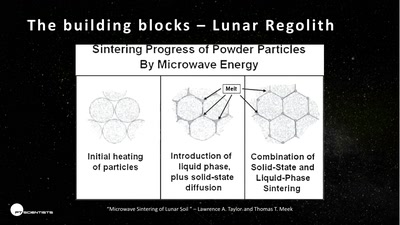
3D printing on the moon
The future of space exploration

56 min
Household, Totalitarianism and Cyberspace
Philosophical Perspectives on Privacy Drawing on the…

120 min
Hacken, dass...?
Ack, die Wette gilt!

55 min
Nach der Coronakrise ist mitten in der Klimakrise
Wege aus der Klimakrise - Was uns droht und was getan…

44 min