Search for "623" returned 2035 results

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities
54 min
Unsupervised Pleasures
Intersectional Language Models for Queer Futures
115 min
Vierjahresrückblick des CCC
Nix los und viel zu tun

47 min
flow3r Badge
Frag die Teams
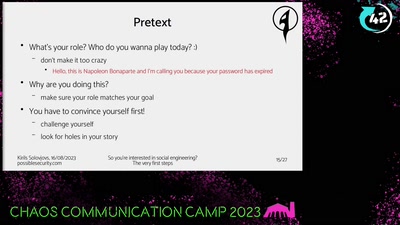
44 min
So you're interested in social engineering?
The very first steps

29 min
What de.fac2?
Attacking an opensource U2F device in 30 minutes or less
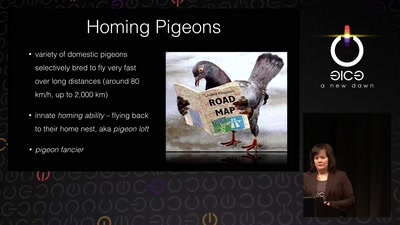
31 min
Living Drones
From war pigeons in 1914 to cyborg moths in 2014

33 min
Retail Surveillance / Retail Countersurveillance
50 most unwanted retail surveillance technologies / 50 most…

33 min
Hacking as Artistic Practice
!Mediengruppe Bitnik about their recent works

36 min