Search for ".hev" returned 1877 results

44 min
Disclosure DOs, Disclosure DON'Ts
Pragmatic Advice for Security Researchers

58 min
Hack_Curio
Decoding The Cultures of Hacking One Video at a Time

45 min
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache

46 min
SELECT code_execution FROM * USING SQLite;
--Gaining code execution using a malicious SQLite database
72 min
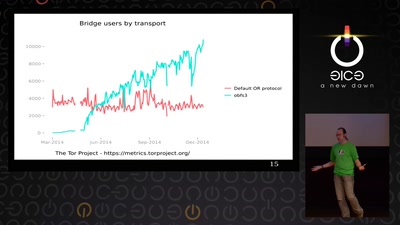
State of the Onion
Neuland
41 min
Our Time in a Product Review Cabal
And the malware and backdoors that came with it.
46 min
Maker Spaces in Favelas - Lecture
Engaging social innovation and social innovators

60 min
the possibility of an army
phone verified accounts bringing the Hessian army back to…
37 min
Code BROWN in the Air
A systemic update of sensitive information that you sniff…
44 min
Alle Roma bleiben
Erfahrungsbericht von Romani Kafava Hamburg

34 min
Social Cooling - big data’s unintended side effect
How the reputation economy is creating data-driven…
62 min
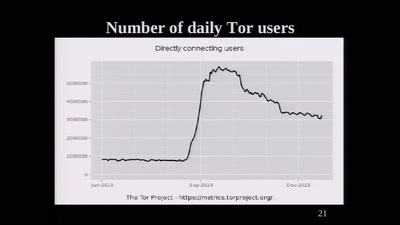
The Tor Network
We're living in interesting times

63 min