Search for "26" returned 4294 results
35 min
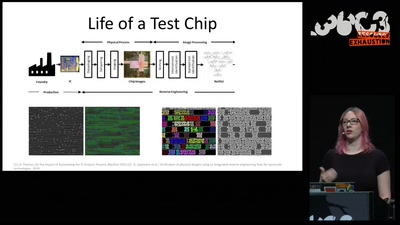
Understanding millions of gates
Introduction to IC reverse engineering for…

61 min
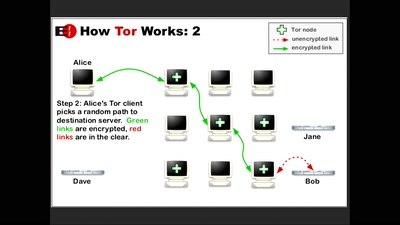
How Alice and Bob meet if they don't like onions
Survey of Network Anonymisation Techniques

70 min
Security Nightmares 0x14
Was Sie schon immer nicht über darüber wissen wollten wer…

30 min
The Machine To Be Another
Exploring identity and empathy through neuroscience,…

63 min
A look into the Mobile Messaging Black Box
A gentle introduction to mobile messaging and subsequent…
27 min
One year of securitarian drift in France
From the Bill on Intelligence to the State of Emergency

58 min
Switches Get Stitches
Industrial System Ownership

26 min
Technomonopolies
How technology is used to subvert and circumvent…

43 min
Sanitizing PCAPs
Fun and games until someone uses IPv6 or TCP

45 min
To Protect And Infect
The militarization of the Internet

41 min
Extracting keys from FPGAs, OTP Tokens and Door Locks
Side-Channel (and other) Attacks in Practice

25 min