Search for "26" returned 4166 results

59 min
De-anonymizing Programmers
Large Scale Authorship Attribution from Executable Binaries…

58 min
Überwachen und Sprache
How to do things with words

60 min
Everything you always wanted to know about Certificate Transparency
(but were afraid to ask)

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

31 min
JODI - Apache is functioning normally
A net.art collective since 1995. Understanding the browser…

63 min
goto fail;
exploring two decades of transport layer insecurity

60 min
The Fight for Encryption in 2016
Crypto fight in the Wake of Apple v. FBI

117 min
Fnord News Show
Wir helfen Euch die Fnords zu sehen.
41 min
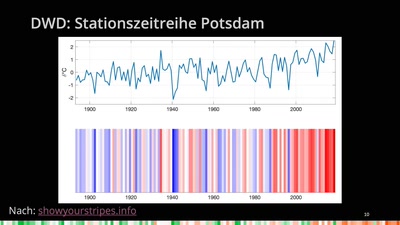
Nutzung öffentlicher Klimadaten
Früher war mehr Schnee

55 min
White-Box Cryptography
Survey

22 min