Search for "20" returned 4812 results

39 min
ID Cards in China: Your Worst Nightmare
In China Your ID Card Knows Everything
58 min
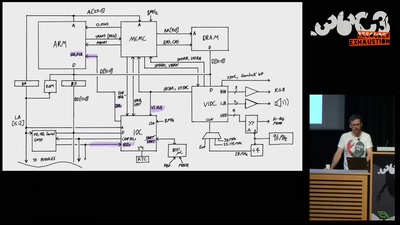
The Ultimate Acorn Archimedes talk
Everything about the Archimedes computer (with zero…

61 min
Beeinflussung durch Künstliche Intelligenz
Über die Banalität der Beeinflussung und das Leben mit…
61 min
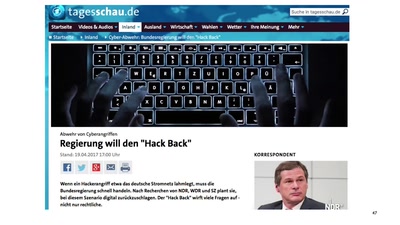
Trügerische Sicherheit
Wie die Überwachung unsere Sicherheit gefährdet

61 min
Trustworthy secure modular operating system engineering
fun(ctional) operating system and security protocol…
33 min
Computer Science in the DPRK
A view into technology on the other side of the world

61 min
Now I sprinkle thee with crypto dust
Internet reengineering session
61 min
Projekt Hannah
Ein open-source Hardware- und Software-Design für…
63 min
Das Assange-Auslieferungsverfahren
Als Prozessbeobachter in London

54 min
A la recherche de l'information perdue
some technofeminist reflections on Wikileaks

57 min
TrustZone-M(eh): Breaking ARMv8-M's security
Hardware attacks on the latest generation of ARM Cortex-M…
26 min
Der 33 Jahrerückblick
Technology and Politics in Congress Talks, from 1984 to now

46 min
CounterStrike
Lawful Interception
25 min
Keys of Fury
Type In Beyond the Scrolling Horizon
60 min
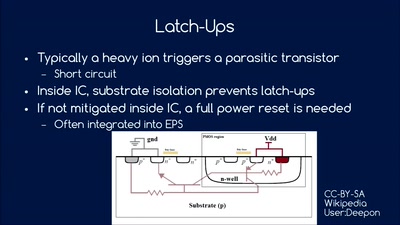
So you want to build a satellite?
How hard can it be? An introduction into CubeSat development
31 min
Trackography
You never read alone

60 min
APT Reports and OPSEC Evolution, or: These are not the APT reports you are looking for
How advanced threat actors learn and change with innovation…

33 min






