Search for "30" returned 4239 results

55 min
What could possibly go wrong with <insert x86 instruction here>?
Side effects include side-channel attacks and bypassing…

60 min
On the insecure nature of turbine control systems in power generation
A security study of turbine control systems in power…

36 min
A Blockchain Picture Book
Blockchain origins and related buzzwords, described in…

14 min
c3 NewsShow
Tag 1

47 min
Hardening hardware and choosing a #goodBIOS
Clean boot every boot - rejecting persistence of malicious…
64 min
Der Deep Learning Hype
Wie lange kann es so weitergehen?
62 min
Space Hacker
Uploading rover...
42 min
Wifibroadcast
How to convert standard wifi dongles into digital broadcast…
62 min
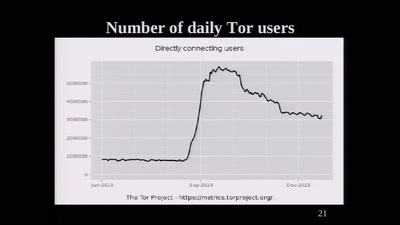
The Tor Network
We're living in interesting times

62 min
Netzpolitik in der Schweiz 2016
Grundrechte per Volksentscheid versenken
26 min
Against Metadata
Twisting time and space to explore the unknown

42 min
Reverse engineering FPGAs
Dissecting FPGAs from bottom up, extracting schematics and…

60 min
osmo-gmr: What's up with sat-phones ?
Piecing together the missing bits
65 min
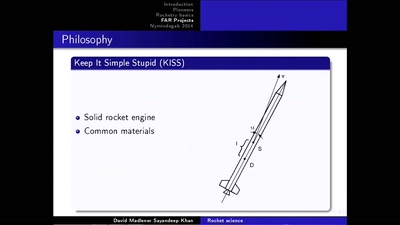
Rocket science – how hard can it be?
First steps into space with sounding rockets

61 min
Zamir Transnational Network und Zagreb Dairy
Das erste computer netzwerk in Krieg (Jugoslavia 1992-1997)
60 min
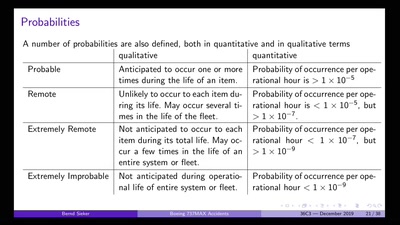
Boeing 737MAX: Automated Crashes
Underestimating the dangers of designing a protection system

38 min