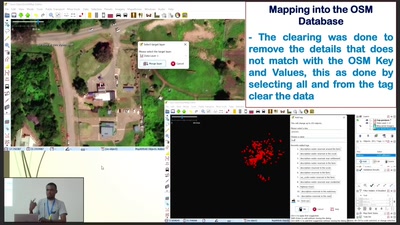
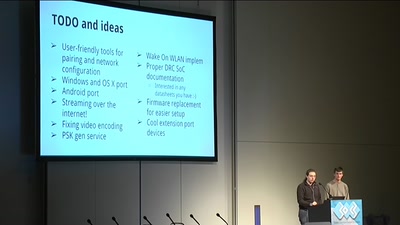
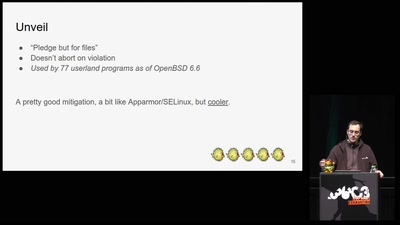
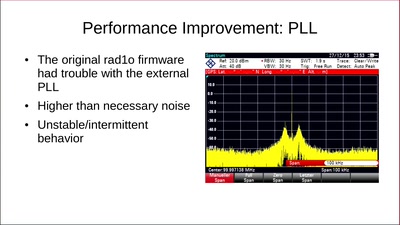
Search for "10" returned 5081 results
61 min
Damn Vulnerable Chemical Process
Exploitation in a new media

55 min
Attribution revolution
Turning copyright upside-down with metadata

44 min
Disclosure DOs, Disclosure DON'Ts
Pragmatic Advice for Security Researchers

55 min
The DROWN Attack
Breaking TLS using SSLv2

64 min
Decoding the LoRa PHY
Dissecting a Modern Wireless Network for the Internet of…

63 min
Das nützlich-unbedenklich Spektrum
Können wir Software bauen, die nützlich /und/ unbedenklich…

49 min
Key-logger, Video, Mouse
How to turn your KVM into a raging key-logging monster

50 min
Internet censorship in the Catalan referendum
Overview of how the state censored and how it got…

51 min
The GNU Name System
A Decentralized PKI For Social Movements

59 min
Visiting The Bear Den
A Journey in the Land of (Cyber-)Espionage
56 min
Rock' em Graphic Cards
Introduction to Heterogeneous Parallel Programming

55 min
Graphs, Drones & Phones
The role of social-graphs for Drones in the War on Terror.
72 min