Search for "15" returned 4930 results

43 min
This is NOT a proposal about mass surveillance!
Analysing the terminology of the UK’s Snooper’s Charter

62 min
„Wir beteiligen uns aktiv an den Diskussionen“
Die digitale „Agenda“ der Bundesregierung aus inhaltlicher,…
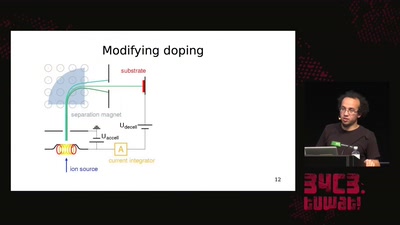
31 min
Trackography
You never read alone
60 min
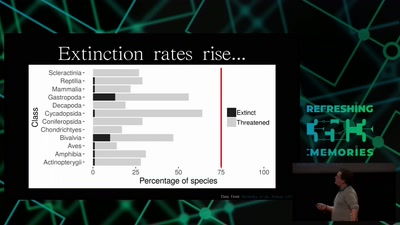
Hacking Ecology
How Data Scientists can help to avoid a sixth global…
25 min
Keys of Fury
Type In Beyond the Scrolling Horizon

60 min
Are machines feminine?
exploring the relations between design and perception of…
33 min
Computer Science in the DPRK
A view into technology on the other side of the world
58 min
Hacking how we see
A way to fix lazy eye?

41 min
NGI Zero: A treasure trove of IT innovation
Resilient. Trustworthy. Sustainably Open.

54 min
World War II Hackers
Stalin's best men, armed with paper and pen

39 min
ID Cards in China: Your Worst Nightmare
In China Your ID Card Knows Everything

30 min
The ArduGuitar
An Arduino Powered Electric Guitar

58 min
Überwachen und Sprache
How to do things with words

49 min
Electromagnetic Threats for Information Security
Ways to Chaos in Digital and Analogue Electronics

58 min
Baseband Exploitation in 2013
Hexagon challenges

58 min
The Magic World of Searchable Symmetric Encryption
A brief introduction to search over encrypted data

60 min
Concepts for global TSCM
getting out of surveillance state mode

62 min