Search for "30" returned 4245 results

58 min
Virtual Machine Introspection
From the Outside Looking In

61 min
Untrusting the CPU
A proposal for secure computing in an age where we cannot…

60 min
From Computation to Consciousness
How computation helps to explain mind, universe and…
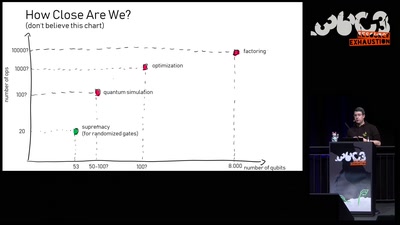
61 min
Quantum Computing: Are we there yet?
An introduction to quantum computing and a review of the…

60 min
Check your privileges!
How to drop more of your privileges to reduce attack…
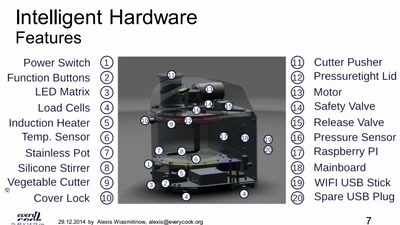
39 min
Why do we need an open food information platform
We want all data about food to be linked and public

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

62 min
The Internet (Doesn't) Need Another Security Guide
Creating Internet Privacy and Security Resources That Don't…

53 min
No Love for the US Gov.
Why Lauri Love’s case is even more important than you…
56 min
Deconstructing a Socialist Lawnmower
Obsolete Technologies + Critical Material Studies in Media…
21 min
Designing PCBs with code
Is designing circuits with code instead of CAD the future…

60 min
Sneaking In Network Security
Enforcing strong network segmentation, without anyone…

54 min
AMD x86 SMU firmware analysis
Do you care about Matroshka processors?

58 min










