Search for "85" returned 3088 results

30 min
Privacy and Consumer Markets
Reversing the Surveillance Business Model

58 min
When hardware must „just work“
An inside look at x86 CPU design

35 min
Harry Potter and the Not-So-Smart Proxy War
Taking a look at a covert CIA virtual fencing solution

58 min
Baseband Exploitation in 2013
Hexagon challenges

58 min
The Magic World of Searchable Symmetric Encryption
A brief introduction to search over encrypted data
60 min
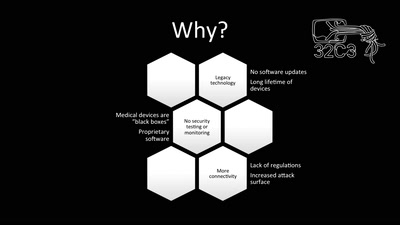
Unpatchable
Living with a vulnerable implanted device

26 min
Hacking the World
The struggle for security for all.

60 min
Buffering sucks!
An attempt of calculating the economic cost of buffering.

46 min
34C3 Abschluss
#tuwat

30 min
The Machine To Be Another
Exploring identity and empathy through neuroscience,…
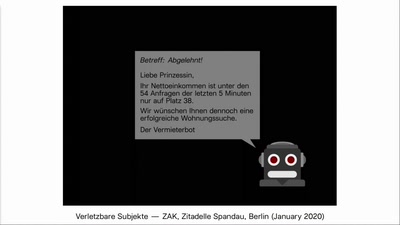
40 min
Wohnungsbot: An Automation-Drama in Three Acts
A media-art project which automates the search for flats in…

51 min
Virtual Secure Boot
Secure Boot support in qemu, kvm and ovmf.

58 min