Search for "20" returned 4645 results
128 min
Methodisch inkorrekt!
Die Wissenschaftsgala vom 32C3
42 min
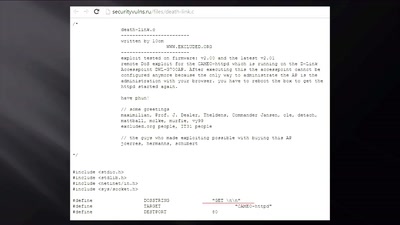
Wifibroadcast
How to convert standard wifi dongles into digital broadcast…

32 min
History and implications of DRM
From tractors to Web standards

39 min
Hacking the Czech Parliament via SMS
A parliamentary drama of 223 actors

42 min
Reverse engineering FPGAs
Dissecting FPGAs from bottom up, extracting schematics and…

54 min
Attacking Chrome IPC
Reliably finding bugs to escape the Chrome sandbox

55 min
What could possibly go wrong with <insert x86 instruction here>?
Side effects include side-channel attacks and bypassing…
29 min
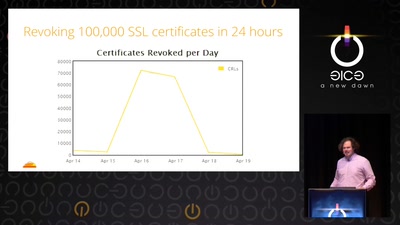
Heartache and Heartbleed: The insider’s perspective on the aftermath of Heartbleed
The untold story of what really happened, how it was…
31 min
GIFs: Tod eines Mediums. Und sein Leben nach dem Tod.
Wie es kommt, dass technischer Fortschritt den Nutzern…

60 min
On the insecure nature of turbine control systems in power generation
A security study of turbine control systems in power…

30 min
Forging the USB armory
Creating an open source secure flash-drive-sized computer
28 min
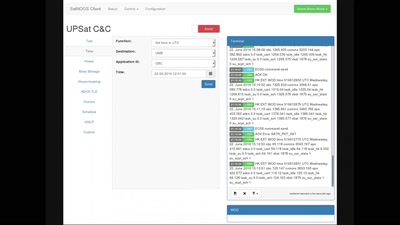
SatNOGS: Crowd-sourced satellite operations
Satellite Open Ground Station Network
31 min
Nerds in the news
Spending a year coding in a newsroom

58 min
CIA vs. Wikileaks
Intimiditation surveillance and other tactics observed and…
60 min
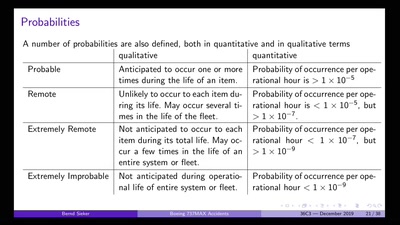
Boeing 737MAX: Automated Crashes
Underestimating the dangers of designing a protection system

60 min