30 min
Shut Up and Take My Money!
The Red Pill of N26 Security

53 min
Console Hacking 2016
PS4: PC Master Race

64 min
Decoding the LoRa PHY
Dissecting a Modern Wireless Network for the Internet of…
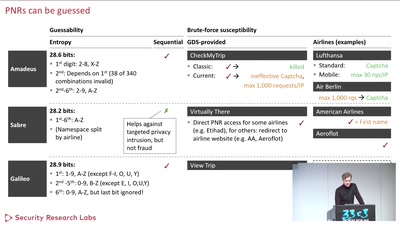
59 min
Where in the World Is Carmen Sandiego?
Becoming a secret travel agent
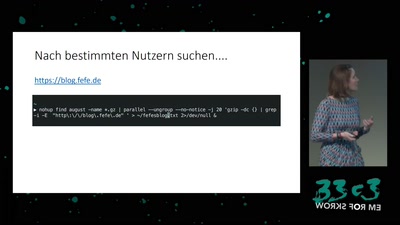
60 min
Build your own NSA
How private companies leak your personal data into the…

33 min
Gone in 60 Milliseconds
Intrusion and Exfiltration in Server-less Architectures

61 min
Nintendo Hacking 2016
Game Over

63 min
A look into the Mobile Messaging Black Box
A gentle introduction to mobile messaging and subsequent…
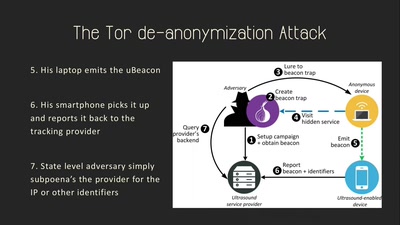
59 min
Talking Behind Your Back
On the Privacy & Security of the Ultrasound Tracking…

61 min
Deploying TLS 1.3: the great, the good and the bad
Improving the encrypted the web, one round-trip at a time

55 min
What could possibly go wrong with <insert x86 instruction here>?
Side effects include side-channel attacks and bypassing…

44 min
Exploiting PHP7 unserialize
teaching a new dog old tricks

62 min
radare demystified
after 1.0

46 min
You can -j REJECT but you can not hide: Global scanning of the IPv6 Internet
Finding interesting targets in 128bit of entropy

29 min
Pegasus internals
Technical Teardown of the Pegasus malware and Trident…

60 min
Everything you always wanted to know about Certificate Transparency
(but were afraid to ask)

59 min
Memory Deduplication: The Curse that Keeps on Giving
A tale of 3 different memory deduplication based…

59 min
Visiting The Bear Den
A Journey in the Land of (Cyber-)Espionage

40 min
Intercoms Hacking
Call the frontdoor to install your backdoors

51 min
Virtual Secure Boot
Secure Boot support in qemu, kvm and ovmf.
64 min
On the Security and Privacy of Modern Single Sign-On in the Web
(Not Only) Attacks on OAuth and OpenID Connect

55 min
The DROWN Attack
Breaking TLS using SSLv2

61 min
Untrusting the CPU
A proposal for secure computing in an age where we cannot…
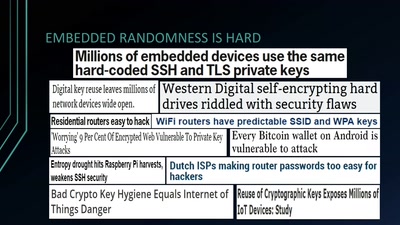
36 min
Wheel of Fortune
Analyzing Embedded OS Random Number Generators
37 min