58 min
Baseband Exploitation in 2013
Hexagon challenges

58 min
Thwarting Evil Maid Attacks
Physically Unclonable Functions for Hardware Tamper…

62 min
To Protect And Infect, Part 2
The militarization of the Internet

47 min
Hardening hardware and choosing a #goodBIOS
Clean boot every boot - rejecting persistence of malicious…
61 min
X Security
It's worse than it looks

46 min
CounterStrike
Lawful Interception
56 min
Electronic Bank Robberies
Stealing Money from ATMs with Malware
58 min
RFID Treehouse of Horror
Hacking City-Wide Access Control Systems

57 min
Kryptographie nach Snowden
Was tun nach der mittelmäßigen Kryptographie-Apokalypse?

45 min
To Protect And Infect
The militarization of the Internet

59 min
Security of the IC Backside
The future of IC analysis

59 min
Zwischen supersicherer Verschlüsselung und Klartext liegt nur ein falsches Bit
Ein Streifzug durch die Fehler in der Kryptografie

40 min
An introduction to Firmware Analysis
Techniques - Tools - Tricks
61 min
25 Jahre Chipkarten-Angriffe
Von der Historie zur Zukunft

47 min
Bug class genocide
Applying science to eliminate 100% of buffer overflows
41 min
SCADA StrangeLove 2
We already know

41 min
Extracting keys from FPGAs, OTP Tokens and Door Locks
Side-Channel (and other) Attacks in Practice
45 min
HbbTV Security
OMG - my Smart TV got pr0wn3d

55 min
White-Box Cryptography
Survey

56 min
WarGames in memory
what is the winning move?

45 min
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache

42 min
Firmware Fat Camp
Embedded Security Using Binary Autotomy

51 min
The GNU Name System
A Decentralized PKI For Social Movements
47 min
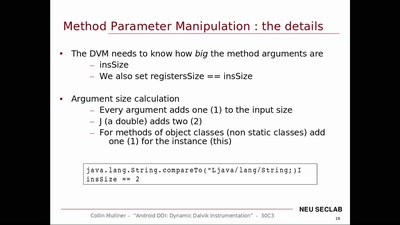
Android DDI
Dynamic Dalvik Instrumentation of Android Applications and…

55 min