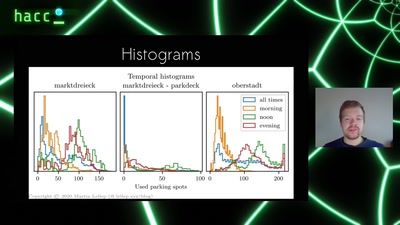
Search for "283" returned 2299 results

58 min
When hardware must „just work“
An inside look at x86 CPU design

58 min
Baseband Exploitation in 2013
Hexagon challenges

90 min
Security Nightmares
Damit Sie auch morgen schlecht von Ihrem Computer träumen.…

60 min
Are machines feminine?
exploring the relations between design and perception of…
60 min
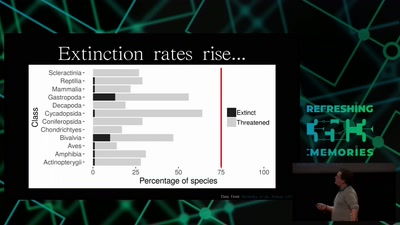
Hacking Ecology
How Data Scientists can help to avoid a sixth global…

62 min
„Wir beteiligen uns aktiv an den Diskussionen“
Die digitale „Agenda“ der Bundesregierung aus inhaltlicher,…
58 min
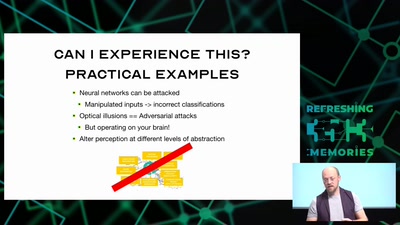
Hacking how we see
A way to fix lazy eye?

58 min
Decoding Contactless (Card) Payments
An Exploration of NFC Transactions and Explanation How…

59 min
Memory Deduplication: The Curse that Keeps on Giving
A tale of 3 different memory deduplication based…

62 min
Corporate surveillance, digital tracking, big data & privacy
How thousands of companies are profiling, categorizing,…

60 min
Concepts for global TSCM
getting out of surveillance state mode

57 min