Search for ".dol" returned 2575 results

40 min
An introduction to Firmware Analysis
Techniques - Tools - Tricks

39 min
DISNOVATION.ORG
Disobedient Innovation
41 min
Framing digital industry into planetary limits and transition policies
The environmental costs of digital industry and pathways to…

57 min
TrustZone-M(eh): Breaking ARMv8-M's security
Hardware attacks on the latest generation of ARM Cortex-M…

49 min
Toward a Cognitive "Quantified Self"
Activity Recognition for the Mind
38 min
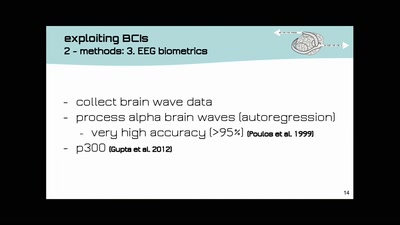
Open-BCI DIY-Neuroscience Maker-Art Mind-Hacking
open source DIY brain-computer-interfaces | technology and…

30 min
In Search of Evidence-Based IT-Security
IT security is largely a science-free field. This needs to…
30 min
Automatically Subtitling the C3
How speech processing helps the CCC subtitle project, and…

30 min
Shut Up and Take My Money!
The Red Pill of N26 Security

58 min
When hardware must „just work“
An inside look at x86 CPU design
31 min
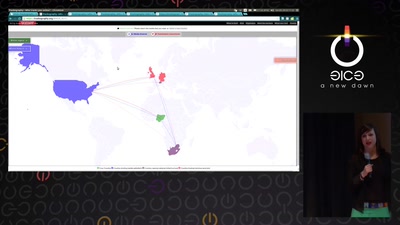
Trackography
You never read alone
32 min
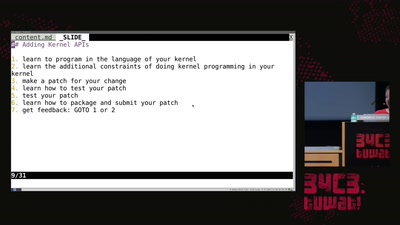
library operating systems
reject the default reality^W abstractions and substitute…

63 min
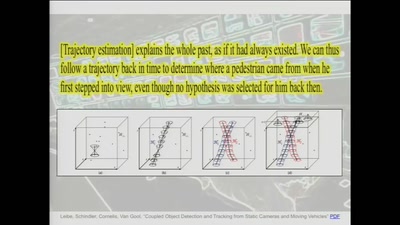
goto fail;
exploring two decades of transport layer insecurity
38 min








![Why we are addicted to lithium [2/2]](https://static.media.ccc.de/media/events/rc3/2021/194-17816a45-eea7-5b85-b623-5f343aec59de.jpg)