Search for "265" returned 2199 results

60 min
Attacking end-to-end email encryption
Efail, other attacks and lessons learned.
58 min
G10, BND-Gesetz und der effektive Schutz vor Grundrechten
Die strategische Fernmeldeüberwachung des BND vor dem…

54 min
Tactical Embodiment
Activism and Performance In Hostile Spaces Online

49 min
Electromagnetic Threats for Information Security
Ways to Chaos in Digital and Analogue Electronics

61 min
Beeinflussung durch Künstliche Intelligenz
Über die Banalität der Beeinflussung und das Leben mit…

63 min
Reconstructing narratives
transparency in the service of justice
62 min
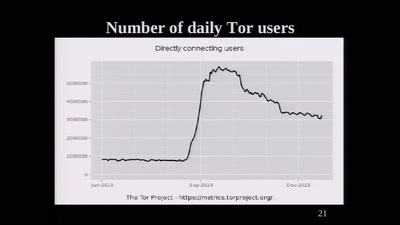
The Tor Network
We're living in interesting times

56 min
Viva la Vita Vida
Hacking the most secure handheld console

62 min
Transhuman Expression
Interdisciplinary research in Painting and Robotics. with…

61 min
Safe and Secure Drivers in High-Level Languages
How to write PCIe drivers in Rust, go, C#, Swift, Haskell,…
64 min
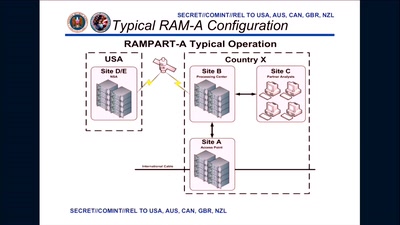
3 Years After Snowden: Is Germany fighting State Surveillance?
A Closer Look at the Political Reactions to Mass…
60 min
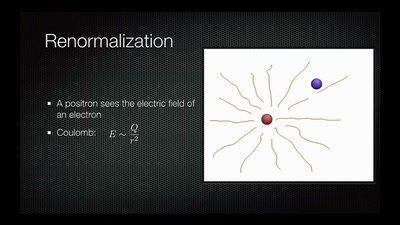
Desperately Seeking Susy
A farewell to a bold proposal?

62 min
Tell no-one
A century of secret deals between the NSA and the telecom…
55 min
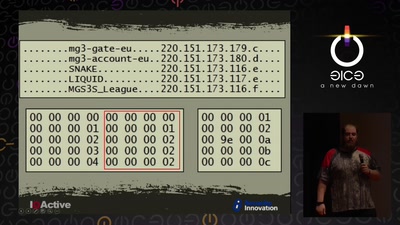
Cyber Necromancy
Reverse Engineering Dead Protocols

60 min
Windows drivers attack surface
some 'new' insights

66 min