Search for "Dan" returned 11216 results

60 min
The rise and fall of Internet voting in Norway
Evaluating a complex cryptographic implementation

64 min
"Exploit" in theater
post-existentialism is the question, not post-privacy

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities
29 min
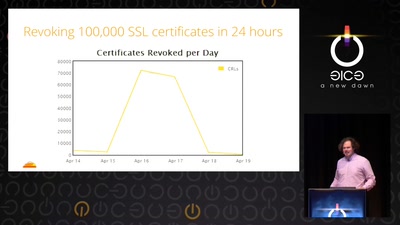
Heartache and Heartbleed: The insider’s perspective on the aftermath of Heartbleed
The untold story of what really happened, how it was…

61 min
Trustworthy secure modular operating system engineering
fun(ctional) operating system and security protocol…

34 min
Snowden Effect vs. Privacy Paradox
Einstellungen und Internetnutzungsverhalten im Kontext des…

60 min
The Only Thing We Know About Cyberspace Is That Its 640x480
One Terabyte of Kilobyte Age
31 min
GIFs: Tod eines Mediums. Und sein Leben nach dem Tod.
Wie es kommt, dass technischer Fortschritt den Nutzern…
31 min
Living Drones
From war pigeons in 1914 to cyborg moths in 2014

61 min
Now I sprinkle thee with crypto dust
Internet reengineering session

61 min
The Invisible Committee Returns with "Fuck Off Google"
Cybernetics, Anti-Terrorism, and the ongoing case against…

62 min
Deine Rechte sind in diesen Freihandelsabkommen nicht verfügbar
Der Protest gegen TTIP und CETA
50 min
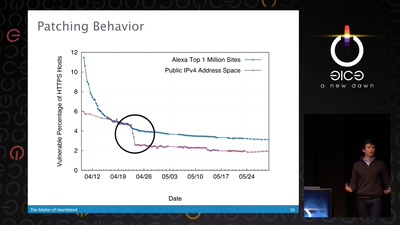
The Matter of Heartbleed
What went wrong, how the Internet reacted, what we can…

60 min
osmo-gmr: What's up with sat-phones ?
Piecing together the missing bits
59 min
NSA Points of Presence in AT
Vortrag mit aktuellen Fotos aus luftigen Perspektiven

30 min
Forging the USB armory
Creating an open source secure flash-drive-sized computer

55 min