Search for "andi" returned 7404 results
68 min
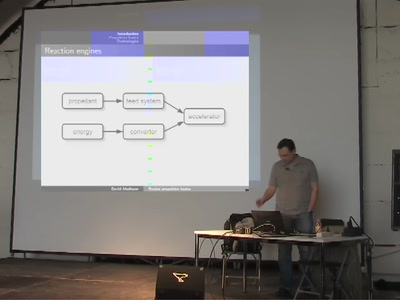
Rocket propulsion basics
An introduction to rocket engines and their application for…

60 min
Glass Hacks
Fun and frightening uses of always-on camera enabled…

50 min
Data Analysis in Terabit Ethernet Traffic
Solutions for monitoring and lawful interception within a…
69 min
DG103: Wikidata
Dive into the free knowledge base and build things with it!

39 min
Digital dissent in Latin America
How the Internet is impacting organizing and dissent in…

43 min
How we changed openSUSE developement
Going from generic distro to stable rolling and feature…
77 min
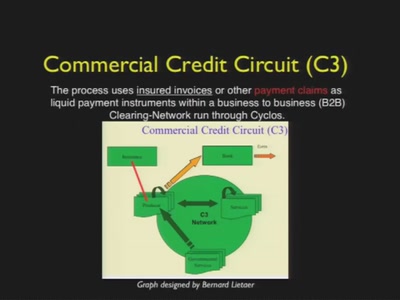
Imagine the Future of Money
Economic transformations, hacker culture and why we should…

93 min
Bluetooth Hacking - The State of The Art
A roundup and live demonstrations of all currently known…
39 min
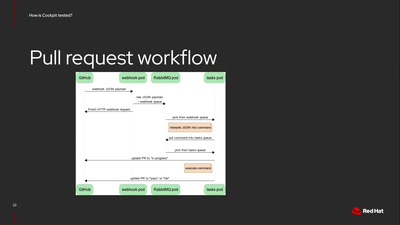
Testing software on multiple Linux distributions
How Cockpit is tested on multiple distributions and…

61 min
Human body as an electric IO system
Hacking your brain, and other body parts. Debunking myths…
33 min
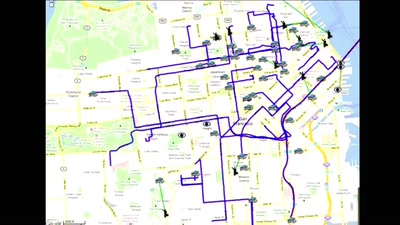
Space making/space shaping
How mapping creates space, shapes cities and our view of…

32 min
Freedom from the web's monopolies
A better architecture for the web, beneficial to both…

30 min
Rowhammer.js: Root privileges for web apps?
A tale of fault attacks on DRAM and attacks on CPU caches
30 min
The philosophy of hacking
Contemplations on the essence of hacking and its…

71 min
Security in the cardholder data processing?!
Experiences and lessons learned with the Payment Card…
57 min
The Small Device C Compiler for 8-bit firmware development
The current state and near-future plans for a central part…

53 min
Fuzzing in the corporate world
The use of fuzzing in the corporate world over the years…
51 min
eSIM management on Qualcomm phones
Using an open-source and mainline Linux stack to work with…
59 min
The Ultimate SPC700 Talk
The hardware behind the music of Super Mario World, Chrono…
26 min
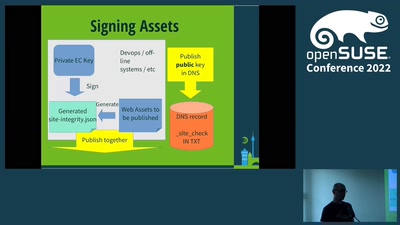
Web asset security
and how to verify that Javascript before you trust your…

46 min
Etherify - bringing the ether back to ethernet
Primitive soft tempest demos: exfiltrating data via leakage…

55 min
Vehicle immobilization revisited
Uncovering and assessing a second authentication mechanism…
40 min
Handsfree assistive technology
My technology portfolio to enable work, life, smart home…
51 min
Playing defence is complicated
What goes into playing defence and what can be holding you…

12 min