Search for "291" returned 2180 results

60 min
Beyond Anti Evil Maid
Making it easier to avoid low-level compromise, and why…

58 min
When hardware must „just work“
An inside look at x86 CPU design

60 min
Concepts for global TSCM
getting out of surveillance state mode

57 min
How I Learned to Stop Reinventing and Love the Wheels
or having FUN with (home/hackerspace) robotics

58 min
Baseband Exploitation in 2013
Hexagon challenges

55 min
White-Box Cryptography
Survey

58 min
Paypals War on Terror
A Historical Re-Enactment of the PayPal14

54 min
How (not) to build autonomous robots
Fables from building a startup in Silicon Valley
61 min
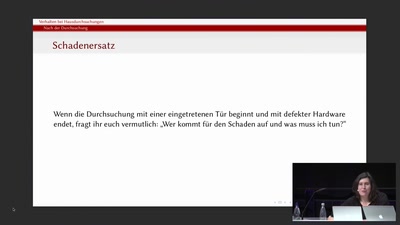
Verhalten bei Hausdurchsuchungen
Praktische Hinweise für den Kontakt mit der Staatsmacht

42 min
A world without blockchain
How (inter)national money transfers works
60 min
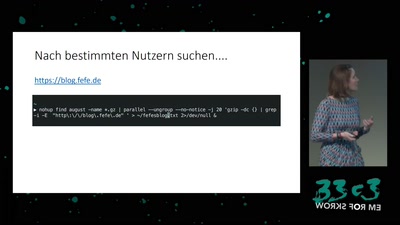
Build your own NSA
How private companies leak your personal data into the…

48 min
REXUS/BEXUS - Rocket and Balloon Experiments for University Students
How to bring student experiments into space.

45 min
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache

113 min
Methodisch inkorrekt!
Die Wissenschaftsgala vom 33C3

61 min