Search for "282" returned 2195 results

58 min
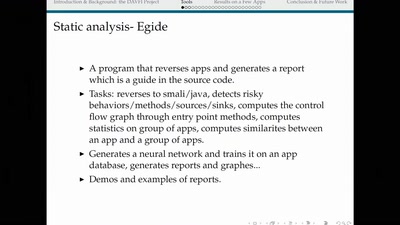
When hardware must „just work“
An inside look at x86 CPU design

55 min
Vehicle immobilization revisited
Uncovering and assessing a second authentication mechanism…

48 min
Don't Ruck Us Too Hard - Owning Ruckus AP Devices
3 different RCE vulnerabilities on Ruckus Wireless access…

60 min
On the insecure nature of turbine control systems in power generation
A security study of turbine control systems in power…

54 min
Attacking Chrome IPC
Reliably finding bugs to escape the Chrome sandbox

32 min
History and implications of DRM
From tractors to Web standards
31 min
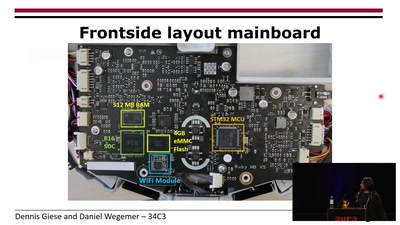
Unleash your smart-home devices: Vacuum Cleaning Robot Hacking
Why is my vacuum as powerful as my smartphone?

53 min
Surveilling the surveillers
About military RF communication surveillance and other…

60 min
Building a high throughput low-latency PCIe based SDR
Lessons learnt implementing PCIe on FPGA for XTRX Software…

32 min
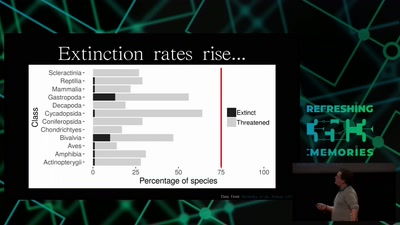
Technology and Mass Atrocity Prevention
Overview on Current Efforts - We Need Moar H4x0rs?!
31 min
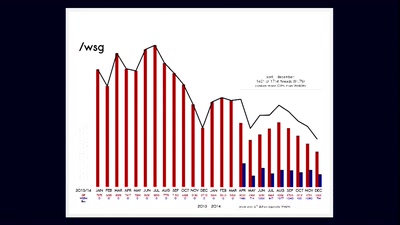
GIFs: Tod eines Mediums. Und sein Leben nach dem Tod.
Wie es kommt, dass technischer Fortschritt den Nutzern…

39 min
Hacking the Czech Parliament via SMS
A parliamentary drama of 223 actors

30 min
Forging the USB armory
Creating an open source secure flash-drive-sized computer

54 min
How (not) to build autonomous robots
Fables from building a startup in Silicon Valley

60 min
Are machines feminine?
exploring the relations between design and perception of…
60 min