Search for "atd" returned 7638 results
74 min
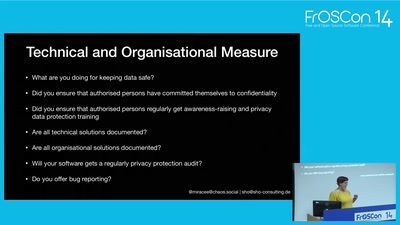
Privacy by design
how to code GDPR and e-privacy regulation safe

25 min
30 seconds to Code
Streamlining development setups with Docker and Open Build…

52 min
The Youth Hostel
An odyssey in the margins of software and paper

66 min
Podjournalism
The Role of Podcasting in Critical and Investigative…
56 min
Hacking ideologies, part 2: Open Source, a capitalist movement
Free Software, Free Drugs and an ethics of death
64 min
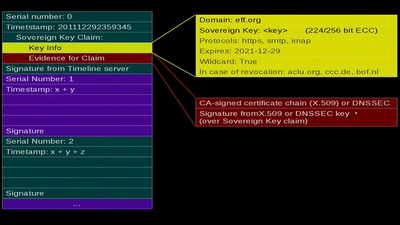
Sovereign Keys
A proposal for fixing attacks on CAs and DNSSEC

62 min
The Internet (Doesn't) Need Another Security Guide
Creating Internet Privacy and Security Resources That Don't…

34 min
Digital Musical Instruments
Evolution and design of new interfaces for musical…
60 min
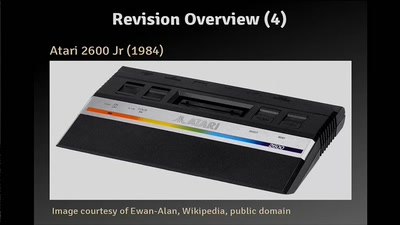
The Atari 2600 Video Computer System: The Ultimate Talk
The history, the hardware and how to write programs
36 min
Long Distance Quantum Communication
Concepts and components for intercontinal communication…

60 min
From Computation to Consciousness
How computation helps to explain mind, universe and…
60 min
An ultrashort history of ultrafast imaging
Featuring the shortest movies and the largest lasers
32 min
spispy: SPI flash device emulation
Open source tools for flash emulation and research

62 min
Transhuman Expression
Interdisciplinary research in Painting and Robotics. with…
60 min
Wind: Off-Grid Services for Everyday People
Integrating nearby and offline connectivity with the…

46 min
Digital Airwaves
Software Defined Radio Basics and some Modulation Theory
47 min
The Realm of Too Many Options
Write, record, mix and actually finish your music
24 min
From Physical to Cloud to Container
One system to deploy and manage them all

20 min
HTCPCP - Networking your Coffeepot
IoT done right for fun and no profit

59 min
8 Years of Config Management
a journey through one company's challenges and learnings

35 min
Weaponized Social
Understanding and tools to mitigate network-scale violences
98 min
Towards automatic end to end mail encryption
mail encryption overview and hands-on Autocrypt sessions

43 min
Pirate Radio
Running a Station and Staying on the Air

30 min
Closing Event
So long and thanks for all the fish

47 min