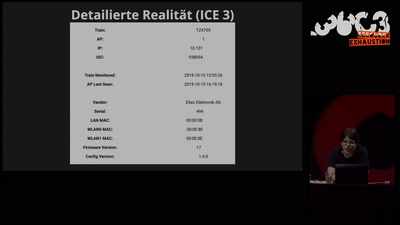
Search for "256" returned 2201 results

40 min
The Great Escape of ESXi
Breaking Out of a Sandboxed Virtual Machine

49 min
C2X: The television will not be revolutionized.
From Cyberfeminism to XenoFeminism

64 min
Source Code and Cross-Domain Authorship Attribution
The Role of Stylometry in Privacy

26 min
Opening Event
35C3: Refreshing Memories
21 min
Designing PCBs with code
Is designing circuits with code instead of CAD the future…

30 min
Shut Up and Take My Money!
The Red Pill of N26 Security
65 min
35C3 Infrastructure Review
Up and to the right: All the statistics about this event…

46 min
Writing secure software
using my blog as example

59 min
TamaGo - bare metal Go framework for ARM SoCs.
Reducing the attack surface with pure embedded Go.
63 min
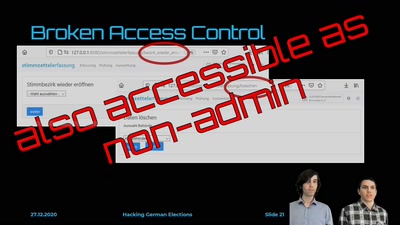
Hacking German Elections
Insecure Electronic Vote Counting - How It Returned and Why…
62 min
Internet, the Business Side
a try to explain the ecosystem
60 min
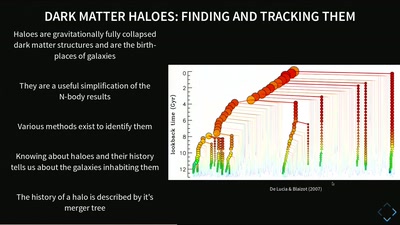
Simulating Universes
What Virtual Universes Can Tell Us About Our Own
60 min
Wind: Off-Grid Services for Everyday People
Integrating nearby and offline connectivity with the…

62 min
radare demystified
after 1.0

64 min
"Exploit" in theater
post-existentialism is the question, not post-privacy

60 min
The Only Thing We Know About Cyberspace Is That Its 640x480
One Terabyte of Kilobyte Age

59 min