Search for "fh"
prev
next

47 min
Trash the prints, print the trash

39 min
A parliamentary drama of 223 actors

52 min
How I Learned to Stop Worrying and Love the Backdoor

63 min
Algorithms define your priorities. Who else besides you can…

60 min
A gentle introduction to post-quantum cryptography

60 min
Evaluating a complex cryptographic implementation
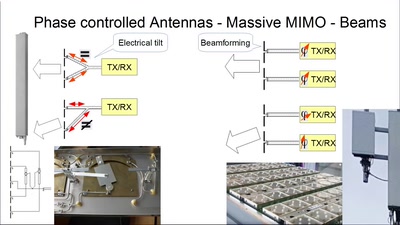
60 min
Die Luftschnittstelle und das Core im Wandel der Zahlen

32 min
Automatic detection of key-reuse vulnerabilities
31 min
From war pigeons in 1914 to cyborg moths in 2014

32 min
A decentralized Public Key Infrastructure that supports…
prev
next





