Search for "582" returned 1912 results

59 min
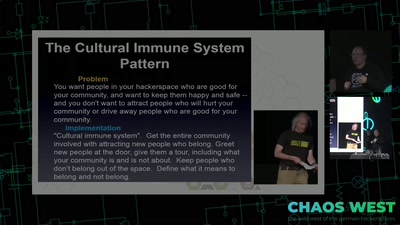
We should share our secrets
Shamir secret sharing: How it works and how to implement it
62 min
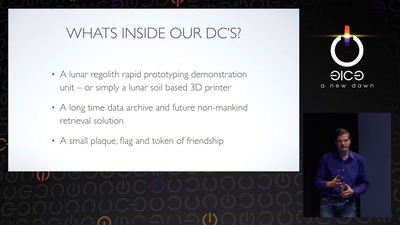
Space Hacker
Uploading rover...
61 min
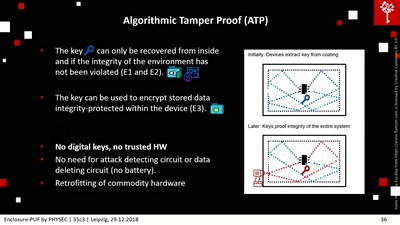
Enclosure-PUF
Tamper Proofing Commodity Hardware and other Applications

59 min
Provable Security
How I learned to stop worrying and love the backdoor

65 min
The Untold Story of Edward Snowden’s Escape from Hong Kong
and How You Can Help the Refugees Who Saved His Life

63 min
Reproducible Builds
Moving Beyond Single Points of Failure for Software…

58 min
PLC-Blaster
Ein Computerwurm für PLCs
41 min
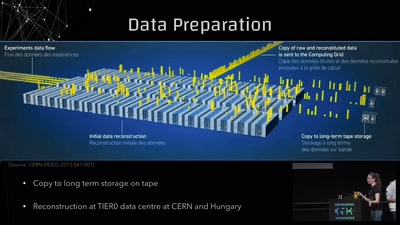
Conquering Large Numbers at the LHC
From 1 000 000 000 000 000 to 10: Breaking down 14 Orders…

47 min
Hardening hardware and choosing a #goodBIOS
Clean boot every boot - rejecting persistence of malicious…
55 min
Cat & Mouse: Evading the Censors in 2018
Preserving access to the open Internet with circumvention…

48 min
Don't Ruck Us Too Hard - Owning Ruckus AP Devices
3 different RCE vulnerabilities on Ruckus Wireless access…

72 min
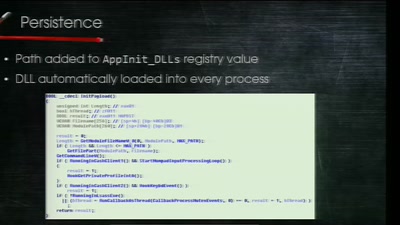
Console Hacking
Breaking the 3DS
56 min