Search for "482" returned 1945 results

55 min
What could possibly go wrong with <insert x86 instruction here>?
Side effects include side-channel attacks and bypassing…
53 min
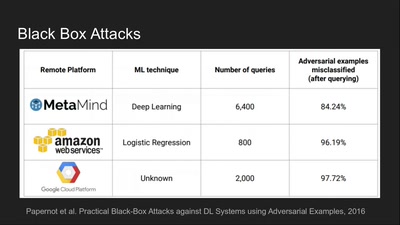
Deep Learning Blindspots
Tools for Fooling the "Black Box"

58 min
Uncertain Concern
How Undocumented Immigrants in the US Navigate Technology

63 min
Don't stop 'til you feel it
Artistic interventions in climate change
59 min
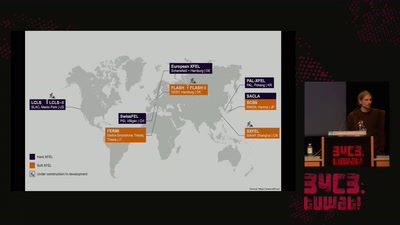
Free Electron Lasers
...or why we need 17 billion Volts to make a picture.

41 min
MicroPython – Python for Microcontrollers
How high-level scripting languages make your hardware…
31 min
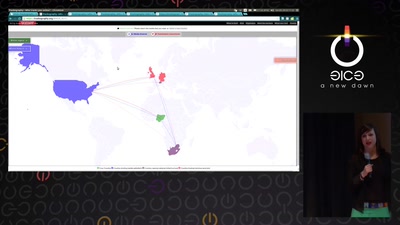
Trackography
You never read alone

60 min
Stromtankstellen – eine neue öffentliche Infrastruktur
Was kann das? Wie kann ich das nutzen? Wo besteht…

55 min
Vehicle immobilization revisited
Uncovering and assessing a second authentication mechanism…

45 min
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache

22 min
Trust us and our business will expand!
Net-activism strategies against fake web companies

46 min
SELECT code_execution FROM * USING SQLite;
--Gaining code execution using a malicious SQLite database

60 min
On the insecure nature of turbine control systems in power generation
A security study of turbine control systems in power…
62 min
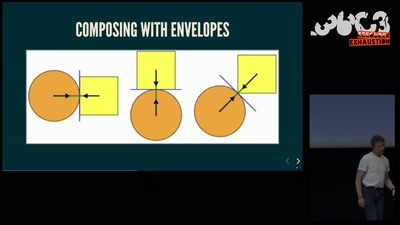
Getting software right with properties, generated tests, and proofs
Evolve your hack into robust software!
60 min
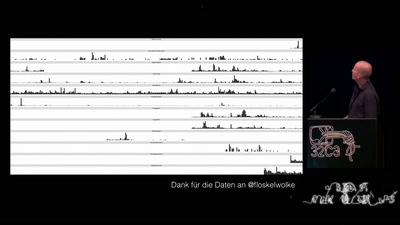
„Nach bestem Wissen und Gewissen“ – Floskeln in der Politik
Politische Phrasologie – warum man aus dem ganzen Zeug, das…
29 min
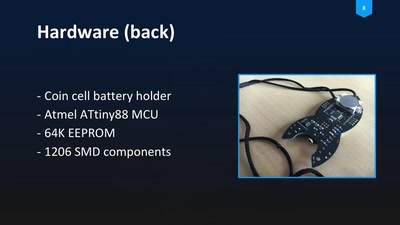
Blinkenrocket!
How to make a community project fly

30 min